Researchers have identified a newly discovered state-sponsored hacking group operating out of North Korea. This group, known as APT43, has been actively targeting government institutions across Europe, the United States, South Korea, and Japan for the last five years.
What is APT43?
APT43, also known as Kimsuky, is a hacking group believed to be operating out of North Korea. The group is known for its sophisticated cyber espionage and theft campaigns, targeting government agencies, educational institutions, and research centers.
According to reports from cybersecurity specialists, APT43 has been active since at least 2018, primarily focusing on strategic data collection related to foreign policy and nuclear weapons programs. Mandiant has identified the group’s ties to North Korea’s ruling elite and personal and geopolitical goals, indicating that its operations align with the state’s interests.
Tactics
APT43 has been observed using various tactics, techniques, and procedures (TTPs) to conduct its cyberattacks. However, a primary method is based on spear-phishing emails, malicious document attachments, and social engineering techniques. For example, emails contain links to sites that redirect victims to fake login pages. Victims input their login credentials, which are then sent to the hackers. This tactic allows APT43 to access the victim’s account and gather intelligence of interest.
Additionally, APT43 leverages the victim’s contact list to launch spear-phishing attacks. APT43’s targets have primarily been organizations in the United States, South Korea, Japan, and Europe, focusing on government agencies and research centers related to foreign policy and nuclear weapons programs. However, the group has also targeted the healthcare industry and pharmaceutical companies. The group has also used backdoors and remote access tools to gain persistence on compromised systems and exfiltrate data.
APT43 Activity
Since the North Korean government does not fund the group, like many North Korean hacker groups, APT43 allegedly finances its activities through theft and cybercrime. Researchers reported in 2023 that the group had stolen over $100 million of cryptocurrency since 2019. The group also uses contact lists stolen from compromised individuals to identify more targets and steal cryptocurrency. The stolen cryptocurrency is laundered using hash rental and cloud-mining services. APT43 is also observed using malicious Android apps that target Chinese users looking to get cryptocurrency loans. Instead, victims lose their digital assets to the threat actors.
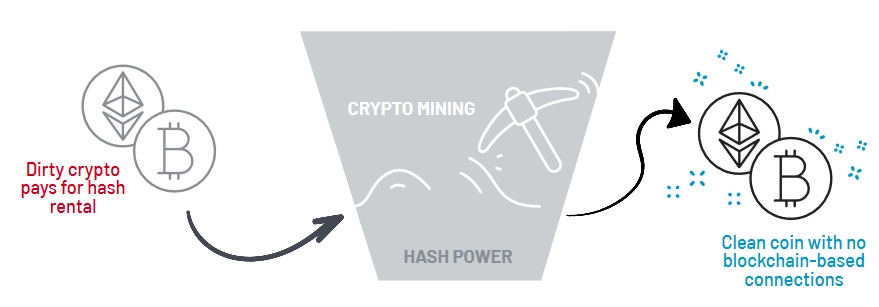
Short scheme of money laundering procedure used by APT43 Source: Mandiant
In conclusion, APT43 is a hacking group that supports the ideology of the North Korean regime. However, by staying vigilant and implementing robust security measures, organizations can better protect themselves against cyber threats. Organizations can take some steps to protect themselves against APT43’s attacks, including implementing strong access controls and password policies, conducting regular security awareness training for employees, and using anti-malware and endpoint protection solutions. It is also essential to regularly patch and update software to address known vulnerabilities.