Ransomware actors have recently been targeting IBM Aspera Faspex, a web-based application used for secure file sharing. According to reports, the attackers are exploiting a vulnerability, designated as CVE-2022-47986, which allows an attacker to remotely execute arbitrary code on the affected server.
What is Aspera Faspex?
Aspera Faspex is a software solution for secure and high-speed file transfer, developed by Aspera, an IBM company. Faspex uses the company’s patented Fast, Adaptive and Secure Protocol (FASP), which is designed to transfer large files and data sets over wide area networks (WANs) with high speed, reliability, and security.
Faspex is a web-based application that allows users to send and receive files through a simple and intuitive web interface, with support for resumable transfers, encryption, and other advanced features. It also provides centralized management of user accounts, transfer policies, and workflows, making it a popular solution for organizations that need to transfer large files quickly and securely across different locations and systems.
Aspera has a large customer base, including many high-profile media and entertainment companies, as well as government agencies, healthcare providers, and research institutions. The company has also partnered with several cloud service providers, such as IBM Cloud and AWS, to offer Aspera-based file transfer solutions on their platforms.
How Does Aspera Faspex Vulnerability Work?
CVE-2022-47986 is a vulnerability in IBM Aspera Faspex, a web-based application used for secure file sharing. The vulnerability allows an attacker to execute arbitrary code remotely on the affected server by exploiting a lack of input validation. Using an obsolete API call, hackers are able to circumvent the authentication and execute any code they want. In particular, several ransomware actors have shown interest in this breach and appear to use it for cyberattacks.
Two most notable of them, IceFire and Buhty, have already succeeded in a chain of attacks. The latter reportedly hacked a chain of servers that were using the vulnerable version of Faspex. IceFire, however, targets Linux infrastructure for the first time in its recorded activity. Previously, it was attacking Windows targets in Arab countries – which is pretty weird behavior either. Overall, the trend for using breaches in file transfer utilities becomes hazardous. Recent attacks of Cl0p ransomware with the use of a breach in GoAnywhere MFT already struck over 130 companies, and no one knows how much ones will they hack having an alternative vulnerability to use.
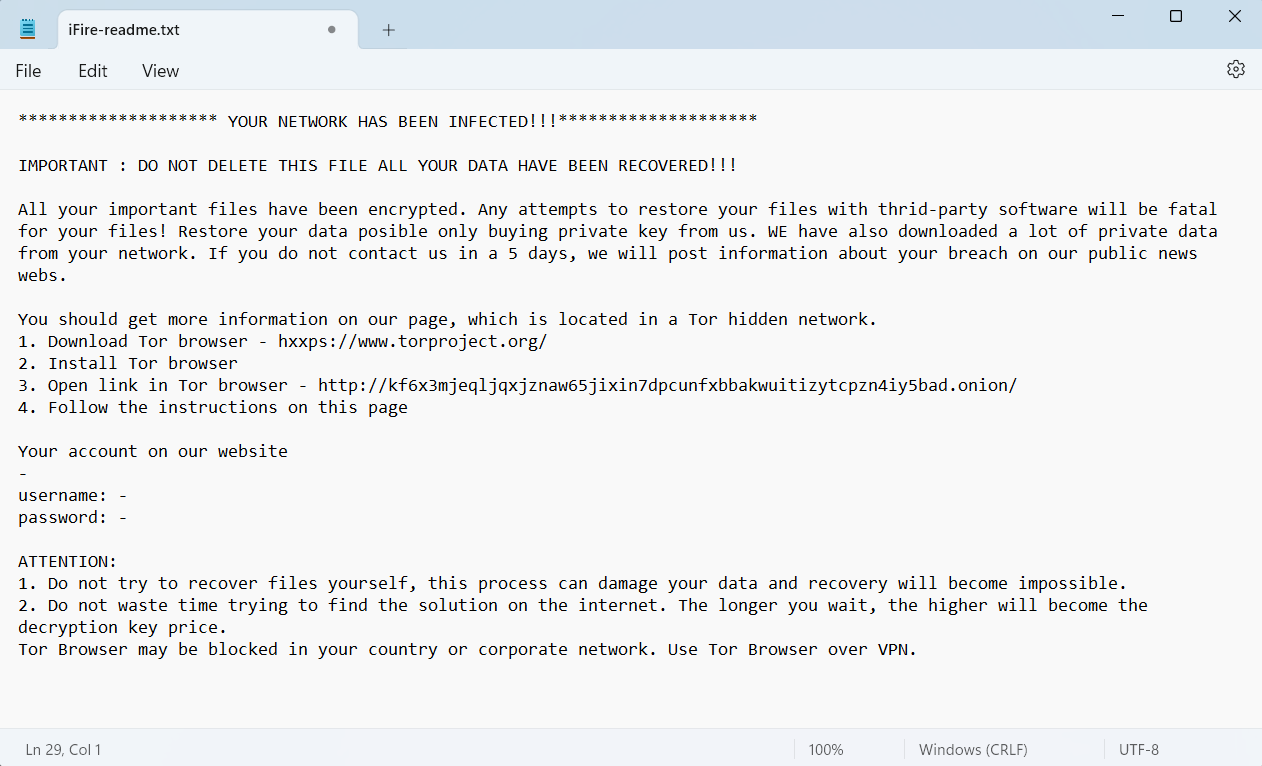
Ransom note left by IceFire ransomware
What can I do?
To mitigate the risk of these attacks, security experts recommend that users of IBM Aspera Faspex patch their systems as soon as possible. In addition, users should follow best practices such as regularly backing up their data and being vigilant for any suspicious activity or emails that could lead to a potential ransomware attack. It is important for organizations to stay informed about the latest threats and vulnerabilities to protect their systems and data from ransomware attacks.