Ransomware is one of the most dangerous types of virus. It encrypts your files, then spams your computer with “readme.txt” files, where you can find the ransom payment guide. Anti-malware software developers are doing their best to intercept this hazardous malware, and to decrypt the files if the attack has been tolerated. This persistent competition is breathtaking, however, the history of ransomware development is exciting, too. Let me tell you, how did ransomware develop, why is it related to trojans and why is it so popular nowadays.
System locker era
First malicious programs that were similar to ransomware appeared in the middle 00s. Windows 7 has just been released, and average knowledge about cybersecurity was on the beginner’s level. People were browsing the Web without any fears. Usually, they were downloading any files they like to avoid losing them in the depth of the Internet. Those days, it was growing day-to-day, so such a threat was more than real. But there was a category of users who decided to profit from such carelessness.
Mentioned users created the programs which were showing the scary banner covering the screen. On this banner, victims have seen a scary message. That could be a note that told about malware appearance, or some scary lines like “your Windows is locked because you browsed the websites forbidden in your country; pay a fine or all your data will be deleted and your PC will be confiscated by FBI”. The way of paying the ransom was described on the same banner. The usual way was a payment to a bank account or mobile phone number top-up.1 However, despite its scariness, it often could be easily closed by stopping the malware process in the Task Manager. If this did not help, you always could try to reboot your PC.
Winlock virus shows a scary banner
Evolution
With the time flow, such malware (also called WinLock) was evolving. It got the ability to intercept the key combinations (Ctrl+Alt+Del) and add itself to the Run registry key. It became impossible to open the Task Manager or interact with the operating system through this banner. However, tricky users found a way to disable the banner. They imitated a shutdown of the computer, having the programs working in the background. Malware was closing together with the system, but before the shutdown, Windows was offering you to stop and save the possibly unsaved data in background programs. Your system was turning back, but the WinLock was already closed. Hence, you could perform actions against it. To avoid WinLock running with the system start, you may use safe mode with command prompt. Actually, this trick still works well against the vast majority of malware.
Final stage before transforming in ransomware
The last (and the hardest in removal) Winlockers got the ability to infect not only the system, but also BIOS/UEFI. Such viruses are launched before Windows, so you have no chance to use the tricks described higher. Because of BIOS integration, these Winlockers are very hard to remove and counteract. The majority of antiviruses cannot fix BIOS changes and delete the malware in it.
How is it distributed?
As it was mentioned, the distribution of such viruses was based on the users’ foolishness. While browsing the Web, you may easily meet abandoned websites/online forums. These pages have no moderation or content review. Therefore, users are free to post any file and any content. No one will check it and delete it in case there is something forbidden or malicious in the message. Inside the files (even if it is PDF, .docx, .xlsx, or .pptx) was hidden, including mentioned Winlock. Besides dubious websites, described malware could easily be got when using the p2p networks or cracked software distribution sites. Such methods are actual up to this day, however, the common name of malware, as well as its behavior have changed.
Modern appearance: trojan-ransom/trojan-encryptor a.k.a. ransomware
First case of ransomware in its “classic” form was spotted in 2012. At the beginning of its way ransom trojans were not considered as a significant danger: antivirus software added a new type of virus in their databases relatively fast. However, malware creators were working on the distribution model of their brainchild, and in 2017-2018 we could see a worldwide ransomware attack. WannaCry virus infected tens of thousands of PCs all over the world, using the vulnerability in the TCP/IP protocol version used in the majority of infected systems. Corporations got the biggest share of total encryption cases, having millions of dollars of loss. Microsoft, who left this vulnerability in the final release of their operating system, started the distribution of a hotfix for this issue. However, companies were quite skeptical about the severity of this virus, so the patch was often installed only after the attack.
Harmfullessness
The main harm that is caused by ransomware is file encryption. Even the oldest versions of WannaCry, STOP/Djvu, Sodinokibi or any other ransomware family are using AES-256 encryption algorithms. That means that there are 2*10^256 possible keys, so there is literally no possibility to decrypt your files with common methods, like brute force. Modern variants of mentioned families use RSA-1024 or even RSA-2048. The last one is considered an encryption standard for all popular web browsers, so that’s no need to explain why it is very hard to decrypt the files which are encrypted with this key.
After the encryption is finished, ransomware will inform you in a specific way. It can be a wallpaper changed to the one where you are told about file encryption, as well as tens of files with money ransom note which can be found in different parts of the file system.
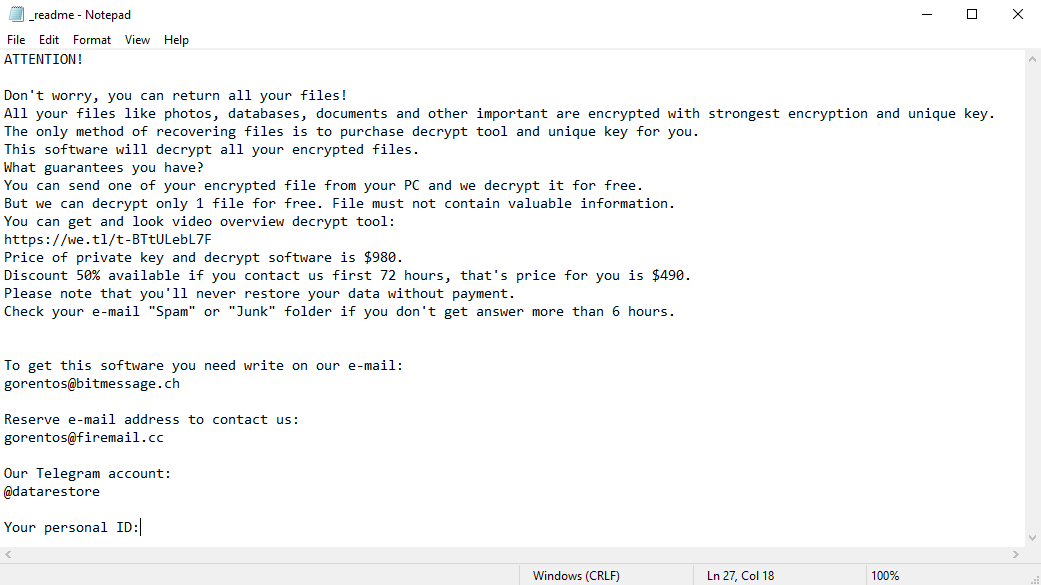
Ransom note created by STOP/Djvu ransomware
Important facts about ransomware families
Ransomware from mentioned families has a lot of common signs, however, there are a lot of differences between them. They are described below:
- Sodinokibi
- WannaCry
- STOP/Djvu
- Dharma
Sodinokibi
Shows you a browser page that tells you that your files have been encrypted; the readme file is named ******-readme.txt, where ****** is a randomized numbers-and-letters bunch. Ransom amount is not specified in the ransom note. Can change the wallpapers on ones where the user is told that his files are encrypted.
WannaCry
Shows you a window of its own program, where the details about decryption/ransom are described. Is able to be injected through vulnerable SMB ports in Windows. Max ransom amount is 600$. Capable of BIOS encryption, so you will see a WannaCry banner instead of a Windows launching process, just like with late-version system lockers.
STOP/Djvu
Summons the readme.txt files only in the folders with the encrypted files. Ransom amount is specified in the readme file (1000$). Makes changes in the deep part of the Windows registry. Capable of browser controlling: browser will be closed immediately in case you try to open any website besides the specified one in the ransom note.
Dharma
Has a single ransom note that is created on the main screen. The extension is quite specific: the email address which is supposed to be used for getting decryption instructions is contained in the extension. In some cases, a readme file can be absent at all.
How ransomware is distributed?
The circumstances are changed, and so did ransomware. As it was mentioned several times, the most massive ransomware attack was committed through the vulnerability of the TCP/IP protocol in Windows. Nowadays, when the majority of systems have the fixing patch installed, ransomware uses other ways of injection. As of fall 2020, all mentioned ransomware families have two main distribution ways: injection through a trojan virus, and injection through false emails.
Trojan viruses are a popular source for all types of malware. These days, such types of malware as stealer, backdoor, worm, adware and browser hijackers are distributed as a pack, and trojan virus acts as a carrier for such a zoo. Such a scheme is very profitable for malware developers, and ransomware is a part of this bundle.
But how are trojans spreading?
The biggest share of trojans distributions is against questionable and dubious programs with sometimes outlaw functionality (program crackers, Windows activators, et cetera). Such apps may have no functionality, as well as have the declared functions, however, there is still a risk that there is something non-declared inside of the installation file with this app. These programs are usually distributed on special websites, which are full of such software, or through peer-to-peer networks – eMule, ThePirateBay, and so on. There is no ability to check if there is any malicious content inside of the program, so its usage is done at one’s own risk.
False emails hold a leading position as a method of ransomware distribution. One day you may see an ordinary email, telling you, for example, about the unpaid fine for parking or the arrived parcel. Inside the letter text, you will see a call to open the attachment. These attachments are a perfect container for ransomware: after opening this file, your PC will be infected. The other suspicious detail is the email address: it does not look like a real email of the local police department or FedEx delivery service, consisting of randomly chosen numbers and letters (like 7ggalwqp@gmail.com). If you saw such a letter in your email, delete it and add its sender to the blacklist.

How can I prevent ransomware injection into my PC?
Mentioned methods of injection can be easily analyzed to figure out the counteraction method. But it is important to assume them and mention several really important ways of avoiding ransomware.
Stop using questionable software. Applications that are created for program cracking are carrying the danger not only because of the possible viruses inside. Cracked software usage is an outlaw action, so in case if the executive authorities spot that fact, they may start a lawsuit that will cost you much more than the price of the license for this program 2.
Do not open any attachments until you are sure that the sender is legit. Organizations will never create a mailbox named “7ggalwqp@gmail.com”, because it can harm the recognition of this company. To check the list of real emails of any company, open the “Contacts” tab on their website.
And the most important advice is to use anti-malware programs. Trojans, which can inject not only ransomware but also a lot of other viruses, are quite easy to remove with specialized programs. Loaris Trojan Remover is one of them. It is capable of fast and effectively detecting and removing hazardous program, saving your system and data of any problems which can be created by viruses.
- About Winlockers on Wikipedia
- More about cracked software danger