Ransomware is the most unpleasant phenomenon for a user. However, it is a gold mine for attackers, as people will pay good money to get their files back. Not surprisingly, news that a particular organization has fallen victim to a ransomware attack frequently appears. Unfortunately, as shows ransomware trends, scammers are not inclined to play the noble game, so without a bit of regret, they target both industrial enterprises and medical or educational organizations. According to statistics, researchers recorded more than 74.2 million attempted ransomware attacks in 2022. This is 20% more than in 2021, which was 61.7 million. As for 2023, ransomware attacks decreased slightly but became more targeted.
2022 Recap
Last year, we identified three ongoing ransomware trends: 1) cross-platform adaptation, 2) industrialization, and 3) geopolitical conflict involvement. These trends have continued, with new multi-platform ransomware families emerging, like RedAlert/N13V and LockBit. Additionally, BlackCat registered domains with names that looked like hacked organizations. This was done to increase ransom pressure on victims. However, the most notorious event of last year was Russia’s full-scale invasion of Ukraine, which also impacted cybercrime. While some cybercriminals tried their best to harm Ukraine, others prohibited using their software against Ukraine. Thus, Eternity Stealer’s author ensured that his malware would not affect users in Ukraine.
Ransomware constantly evolves, with new groups emerging and old ones going dark. For example, last year saw the emergence of RedAlert/N13V, Luna, Sugar, Monster, and BlackBasta. Meanwhile, notorious groups like REvil and Conti have gone dark, but their archives have been leaked and analyzed. Meanwhile, Clop has ramped up its activities and claimed to have hacked 130 organizations using a single zero-day vulnerability. As a result, organizations must be cautious and protect themselves from these evolving threats.
Spreading methods
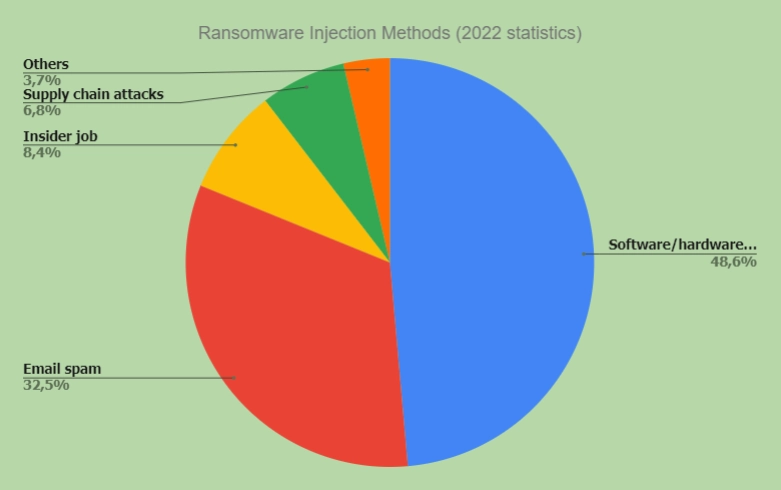
Although in comparison to 2021, in 2022, the share of ransomware by all cybersecurity incidents decreased from 51.9% to 39.8%, it still held the leading position. According to GERT (Global Emergency Response Team) research, almost half of the incidents involved the exploitation of vulnerabilities in publicly available devices and applications. These ranged from broken routers to vulnerable versions of the Log4j logging utility. At second place were malicious emails and compromised accounts. In addition to the methods above, there is a risk of receiving an unexpected gift through insiders or a supply chain attack. These cyber-attacks focus on the weaker links in the organization’s supply chain. Thus, attackers exploit organizations’ trust in third-party suppliers, making a cyberattack more successful.
But what almost stays the same is using specific tools that hackers use. As a result, ransomware groups have consistently used the same tools year after year. These tools include PowerShell for data collection, Mimikatz for privilege escalation, PsExec for remote command execution, and frameworks such as Cobalt Strike for all attack stages.
What about 2023?
Based on the above, we can assume what we should expect in the second half 2023. First and foremost is the expansion of malware functionality, something that ransomware groups have been doing since 2022. For example, the Play ransomware collects different SMB-enabled IP addresses, then establishes a connection and mounts SMB resources. This allows it to copy itself onto target machines and run on them. In addition, BlackBasta started using the LDAP library to get a list of available devices on the network. Finally, LockBit added a credential-dumping feature, allowing tools like PsExec to run automatically. However, this has been removed in later versions. Nevertheless, most notorious ransomware groups have tended to introduce “self-spreading” features, making life easier for operators.
Cyber Communism
While someone is trying to revive something long dead, the significant ransomware gangs see the upside. They operate on the principle of communism. That is, they borrow features either from leaked code or from code acquired from other cybercriminals, thus improving the functionality of their own malware. Therefore, LockBit released a new version based entirely on the leaked Conti code. Such “cooperation” between ransomware gangs only improved their actions. The groups have teamed up and are working to improve their attacks and develop advanced strategies to bypass security measures. Unfortunately, this ransomware trends has resulted in high-quality hacking tools that other ransomware companies can buy on the Darknet.
Exploitation of vulnerable drivers
The old but gold tactic of abusing a vulnerable driver still works well, especially with antivirus drivers. For example, AvosLocker exploited Avast kernel driver vulnerabilities and newly described vulnerabilities that the ransomware Cuba exploited in addition to AvosLocker. In addition to AV drivers, the researchers reported that ransomware used Genshin Impact anti-cheat drivers to bypass endpoint protection on the target device. The most unusual method the researchers reported was the use of a leaked legitimate Nvidia certificate and a Kuwait Telecommunication Company certificate. Thus, the intruder used it to sign a malicious rawdisk driver used in wiper attacks on Albanian organizations.
Network protocol vulnerabilities
A network vulnerability refers to a weakness or flaw that can be used to gain unauthorized access and launch various attacks. These weaknesses can be found in hardware, software, or configuration settings. Since the beginning of 2023, this niche has attracted increased interest. For example, the RCE vulnerability in MSMQ service allows an attacker to remotely run code without authorization. This can be done by accessing the TCP port 1801. Thus, an attacker can take control of the process by sending a single packet with the exploit to the 1801/tcp port, thereby triggering the vulnerability. Another example is the SLP vulnerability. It allows the attacker to use spoofed UDP traffic to amplify the request volume and conduct a denial-of-service attack. Amplification factor may reach an enormous number of 2,200 – frankly unseen ever before. Network vulnerabilities are always at risk of hacking as attackers try to exploit them and gain access to business systems.
How to protect yourself?
Ransomware tactics are nothing new, so cyber criminals have had time to refine their skills. However, technology is improving, and effective methods are becoming even more effective. To get more profit, ransomware groups are targeting more platforms, including macOS, FreeBSD, and unconventional CPU architectures like MIPS and SPARC. Therefore, organizations and security professionals should stay vigilant and adapt their strategies to outsmart evolving ransomware trends. As a result, to stay ahead of ransomware actors’ ever-changing strategy, we have some tips:
- Keep their software up to date. It prevents infection through vulnerability exploitation, one of the most common initial infection vectors ransomware actors use.
- Keep their SOC or information security teams up to date with the latest ransomware tactics and techniques.
- Use security solutions tailored to safeguard their infrastructure from various threats. For example, anti-ransomware tools, EDR, and targeted attack protection.