Script-based malware is not a new thing at all, but can definitely be called “new” when we talk about its modern appearance. Scripts were used over a decade ago to deliver malware or do some unpleasant things on infected computers. But their modern nature has changed.
Around the edge of the ‘10s, antivirus tools made a large leap forward in detection quality. The detection rules were applied for the whole malware classes, instead of banning the subtypes or even exact strains. Malware analysts did a great job, and it resulted in serious effects on viruses, worms, script-based malware and some other nasty stuff. Nonetheless, that was not an obstacle for making some of them return.
What is Script-Based Malware: Defenition
Scripts are simple programs that are created using one of the scripting languages. Python, JScript, Visual Basic, Bash, PHP or Ruby – choose whatever you want. All of them are quite easy to study for the beginner level – and that will be enough to create a script. They are very useful when we talk about speeding up the workflow, or making the workstation roll-out process faster. But besides being a useful and benevolent tool in the hands of system administrators or amateurs – cybercriminals put an eye on them either.
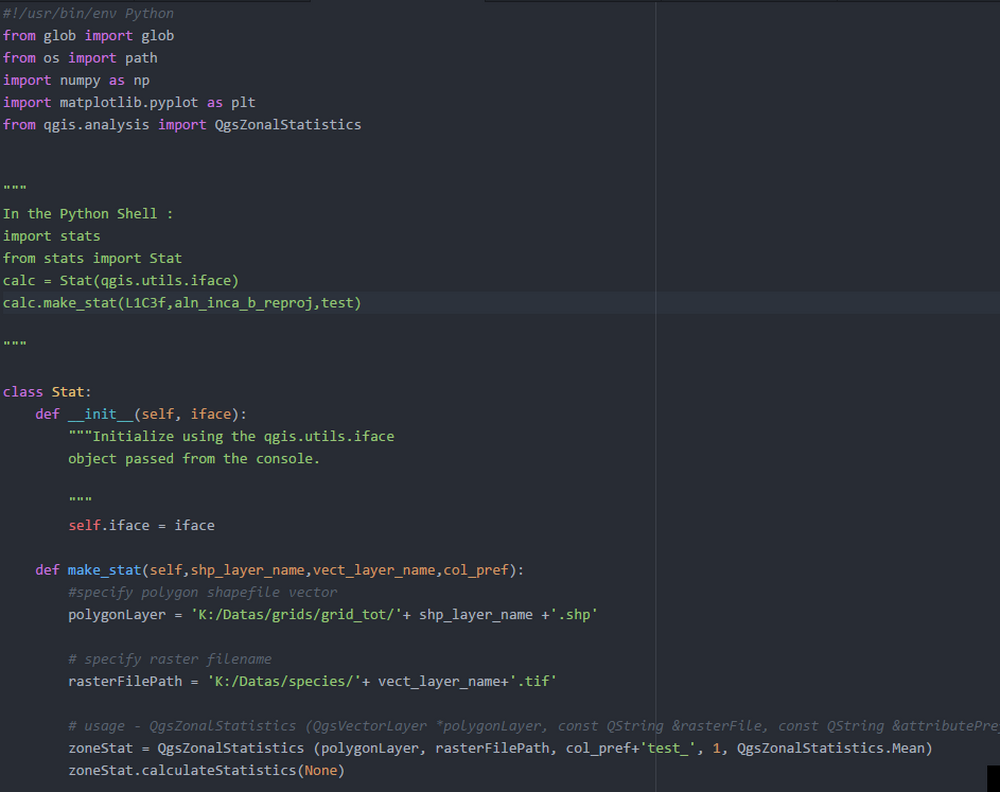
Of course, fraudsters do not stop on being script kiddies – the process of hiding the malware into a script is not an easy thing. In fact, it was pretty easy in the times when scripts contained the exact malware. But now, script-based malware is only delivered by those scripts. That gives the crooks the ability to bypass the antivirus detection rules and successfully deploy the payload. Even more troubling is that scripts are usually executed through a PowerShell, that allows malware to be downloaded and launched without a single sign.
Modern Script-Based Malware. How Does it Work?
Script-based malware, exactly, did a sly trick. Instead of thinking about more complicated ways of masking the malicious stuff, they just made these scripts a downloader malware. This malware type usually makes the system weaker and then injects malware, but not in the case of scripts. They have no need to stop your Defender or third-party security tool. Attacks done with the use of script-based malware usually belong to fileless attacks. That means that both initial malware and the payload it delivers are located inside of RAM – without any paths on your disk1. That makes antiviruses without a specifically-designed heuristic engine useless against script-based malware.
Injection
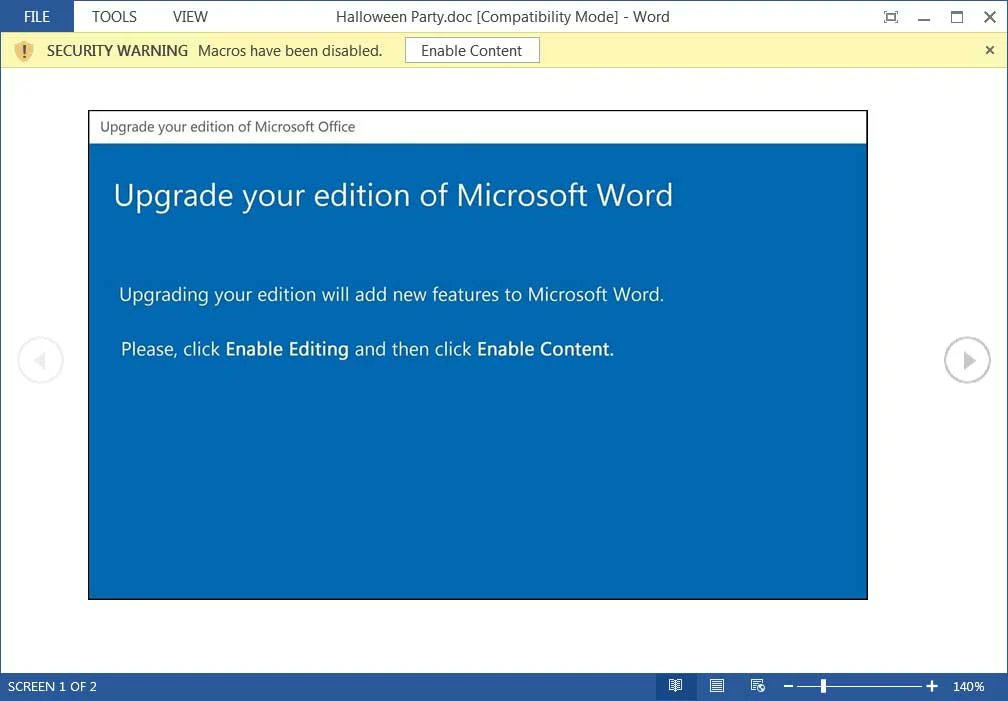
These days, the initial script usually appears on your computer through 2 ways – bait emails and unlegit software. Email messages that trick you to open the attached document contain the exact script as a MS Office macro, or a part of an HTA or PDF file. Unlegit software, on the other hand, mask the attack in the other way. Since these nasty pieces of software (keygens, hacktools, etc) often contain the parts that must be run manually, it is very easy to put a script among these parts.
In rare cases, malicious scripts can appear on online forums, especially on the ones that offer guides for newbies in programming. They can be substituted with Discord or Telegram chats, but the effect is always the same – this script is on your PC and it does its dirty job.
Action
The biggest danger of script-based malware hides in what it can do without even a single noise. As I have mentioned, your system executes the scripts through the PowerShell. This console tool allows seamless operations with commands and scripts. You don’t see the notifications or windows that could be the “marker” of malware presence. Thus, you will likely not be able to do a thing if the script-based malware was started.
Script execution in PowerShell
How Dangerous Is It?
All malware is dangerous – just remember this thesis as an axiom. And one that appears after the script activity is even more dangerous. Such an attack is usually pre-planned, and requires a bit more resources than usual malware spreading campaigns. Hence, it is obvious that fraudsters wish to receive much more profit from this operation. Ransomware, spyware, coin miners – that is not the full list of possible malware that can appear in your computer.
It is noticeable that script-based malware does not create a lot of impact to your system. Any changes in the OS configuration go against the script stealthiness. Hence, crooks avoid any tricks with Defender or Group Policies, that are pretty usual for other malware injection ways. Meanwhile, they still sometimes use so-called system cleaners (CCleaner, for example) to remove your security tools. They just inject it together with the initial malware pack, and remove your antivirus before running the payload.
How to Protect Your System From Script-based Malware?
It is not as easy as with “regular” malware. Since scripts and all things that are related to them exist only in the RAM, the designated anti-malware program must have a more precious heuristic detection engine. Basic scans will not bring any effect, regardless of the database’s quality. Another way to stop the script-based malware is to prevent the initial script from launching. Antivirus programs with a zero-trust policy can do this – but it is hard to find one for individuals. The only widespread anti-malware program that applies this technology is Microsoft Defender – but it is far from being ideal in other aspects.
That’s why I’d recommend you to rely on yourself, exactly, on your attentiveness. In the case when antivirus software is generally useless, that is the only remedy. For instance, avoid websites with pirated software. Those pages are known for distributing ransomware, miners and other nasty stuff. Email messages you receive also must be checked with special attention. Things like Amazon delivery notifications or emails about changes in banking policies from the financial institution are often counterfeited. Exactly, the attachments in these messages contain the subject of this article.
- Read more about fileless malware attacks on Wikipedia.