SQL injection is a major threat to the data security. Hackers can get a lot of important information in just a couple of queries – isn’t it a nightmare? In this article, we will look into SQL Injections to understand what we might encounter online. Consider the types of SQL Injection and the solutions to prevent it.
What is SQL injection (SQLi)?
SQL Injection is one of the most common vectors of database attack and information that is not designed to display. To carry out this attack, malicious SQL code is used to manipulate the same database, which includes information about any elements.
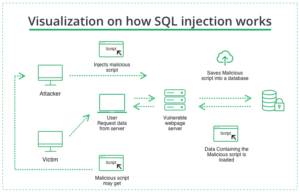
Visualization on how SQL injection works
Among these elements are privacy of company data, personal data of users, and the list of users. The results of successful SQL injection are deplorable. The attacker can get unauthorized viewing of user lists and others.
 Is a real RED light for the different kinds of spyware
Is a real RED light for the different kinds of spyware
What are SQL queries
SQL is a declared programming language for modifying, creating, and managing data in a relational database, which also implies the use of an appropriate database management system. Operators perform SQL queries for different tasks, such as updating and deleting records and extracting commands.
To perform these tasks, you must use SQL elements, such as queries using the SELECT statement. This command allows you to extract data that corresponds to your specific settings. Below is one of the most common SQL queries that look like this:
SELECT ItemName, ItemDescription
FROM Item
WHERE ItemNumber = ItemNumberYou can create a string query from this Web application, which is then sent to the database as a single SQL statement:
sql_query= "
SELECT ItemName, ItemDescription
FROM Item
WHERE ItemNumber = " & Request.QueryString("ItemID")Then the user input items/items.asp?itemid=999 can create the following SQL query.
SELECT ItemName, ItemDescription
FROM Item
WHERE ItemNumber = 999SQL Injections Example
In general, you can undress SQL Injection attack examples into three categories: In-band SQLi (Classic), Out-of-band SQLi, and Inferential SQLi (Blind). SQL injections depend on the different methods of accessing server data and its ultimate damage.
In-band SQLi
To launch their attack and collect its results, the attacker uses the same communication channel. Analysts name it the most common, because of the simple and efficient method of work. But this method is divided into two more subtypes:
- error-based SQLi – In this case, the hacker performs the actions for which the database starts to give error messages. Data from such messages gives the attacker enough information about the structure of the database.
- Union-based SQLi – this method often uses only the operator of the UNION SQL to get a single HTTP response. It does this by combining several choice operators that are generated by the database.
Inferential (Blind) SQLi
Here the attacker sends useful data to the server to get more information about its structure and monitors the behavior and responses of the given server. In real-time, the attacker cannot see the full amount of information about the attack. Database simply doesn’t pass the data to the attacker on its demand. Actually, that is the reason why this method received its name. Blind SQL injections run much slower because they rely on the server’s behavior and reaction. Blind SQL injections classification is present below:
- Boolean – in this case, the attacker suggests the application to return the result in response to the SQL query to the database. The original result depends on the request type: false or true. Whether the HTTP Response gots the changes also depends on the result. Therefore, only then will the attacker be able to know whether the message was false or true.
- Time-based – the request sent by the attacker, in this case, causes the database to wait (within a few seconds) before reacting to it. And thanks to this waiting period, the attacker can understand whether the request was true or false. Next, the initial result will affect the generation of the HTTP response, whether it will be instantaneous or will occur after some time has elapsed. In this case, the attacker does not need to rely on the database, as he can find out through the received false or true value thanks to the message he used.
Out-of-band SQLi
Attackers can use this form when the specific features of the database server for integration with the web application are present. This attack is alternative to the in-band and inferential SQLi techniques. An attacker uses Out-of-band SQLi only if he cannot use the same channel to launch an attack and collect information. That situation is typical when the server is too unstable and slow to perform such actions.
What is the Purpose of SQL injection attacks?
SQLi attacks are well known in the cybersecurity industry for their reputation. Many large companies have spent a lot of effort to discover these threats and counteract them. In order to avoid SQLi attacks, you should understand what to fear. First of all, hackers are aimed at changing the entered data and at the same time creating malicious queries.
Adding partial SQL query elements to the user name field helps a hacker to make the database display, and thus have access to important data that only an administrator has access to. Do not forget that in the case of a successful attack, the hacker will be able to steal confidential data. Cell phone numbers, credit card details, addresses – your clients won’t be happy. But the most common target of this attack is still better to consider websites.
How to Prevent SQL Injection Attacks?
There are different methods to prevent an attack, such as the use of modern technologies, updating platform sites, the use of plugins, and more. But if you want to take a closer look at website security, then below we will look at some tips for preventing SQL injections:
- Don’t forget the updates. Attackers need to find more vulnerabilities on your device or in your network to increase their chances of a successful attack. They use SQLi to identify alleged violations and then use them to launch cyber attacks.
But updates can contain vulnerability correction, but significantly reduces the chances of hackers successfully conducting a cyberattack. So don’t forget to keep up with the latest updates of your operating systems, introduce new features and fix various bugs, it will become your good habit and useful problem prevention. - Restrict & Sanitize Inputs. Restrictions on input data will significantly reduce the risk of intrusion on your PC. Set these limits and the database will weed out all requests that hackers will try to send. Examples of this can be setting only letters and characters for the user name or only certain numbers for the phone number.
- Keep sensitive data encrypted. Open passwords are another good way to let a hacker access your database. To prevent this from happening, don’t keep your passwords clear. Try to turn your password into a complex algorithm, include a random string of characters, and encrypt them.
- Users should not see specific error messages. Do not let hackers see specific problems or errors in your database. If you even inform users of an error, don’t share the details. Do not mention the nature or type of the error. It will also be useful to configure failed requests and error logging.
- Use a special Scanner to Detect SQL Vulnerabilities. Nowadays, device security developers provide us with a large number of tools for scanning sites and applications. We, in turn, can not neglect this and protect ourselves by using one of these tools. With this, you can perform various vulnerability tests for SQL-injection attacks. This way you will know about the alleged threat and you will be able to prevent it.