Lately the research came out done by Splunk on what is the fastest ransomware family out there? They tried to test what ransomware sample will do the quickest in time encryption of the files.
How Long it Takes for Ransomware to Encrypt the System?
The results of this research coincided with a similar only marketing PR stunt from the LockBit gang. They also compared different ransomware families on what is the fastest. Their own ransomware software turned out to be the fastest.
Researchers from Splunk claim that the results of this research will help the defenders to make more precise decisions concerning the ransomware threat. And in general, it’s quite interesting to see whether it is possible to stop the full encryption after the infection and what is more important how much time we have in such a case.The research was conducted in the specially controlled environment with the simulation of the event of a real infection. Researchers picked up ten variants from ten different malware families. The total amount of files made up in a whole 53 GB. The files all 98,561 had different file extensions like pdf, XLS, doc.
Every ransomware sample was tested across all four hosts amounting to 400 different ransomware runs. To put simple 10 families x 10 samples per family x 4 profiles. To collect the needed data researchers used a combination of Microsoft Sysmon, stoQ, Zeek along with Windows Perfmon statistics and native Windows logging.
“In our initial hypothesis, we asserted that if ransomware executes on a system, then it’s too late for an organization to respond effectively. We conducted a literature review of ransomware encryption speed and only uncovered work that was encyclopedic in scope from one of the ransomware groups themselves,” goes in an article written on the team’s blog.
What is the Fastest Ransomware Was Conducted?
So the team created four different “victims” machines that consisted of Windows Server 2019 and Windows 10 operating systems. It should be noted each had its own two different performance spécifications imitating customer environments.
All samples that were taken for the test researchers received from Microsoft Defender detection identifiers on VirusTotal.

To capture the needed encryption events researchers enabled Object Level Auditing on 100 directories where their files were put to test. This in its turn provided the team with EventCode 4663 logs that they used to calculate the Total Time to Encryption (TTE) for each sample correspondingly.
While testing the samples researchers got an access to Accesses value of DELETE at the end of each encrypted file from each sample. And that is how they measured encryption speed. However researchers warn that not with every ransomware you get this and a search for EventCode=4663 Accesses=DELETE in Splunk doesn’t always give you the same results.
The Results of the Research
The results of the research turned out to be as the LockBit gang “advertised” on its Tor site. The ransomware family from these criminal developers encrypted the test files in four minutes and nine seconds. Babuk took the second place with one minute behind.
But it’s important to understand the placement of the ransomware runners was done according to the median duration as some families’ sample results would mess up the average duration. To explain, researchers named one sample from Babuk ransomware that took to encrypt the files more than three and a half hours.
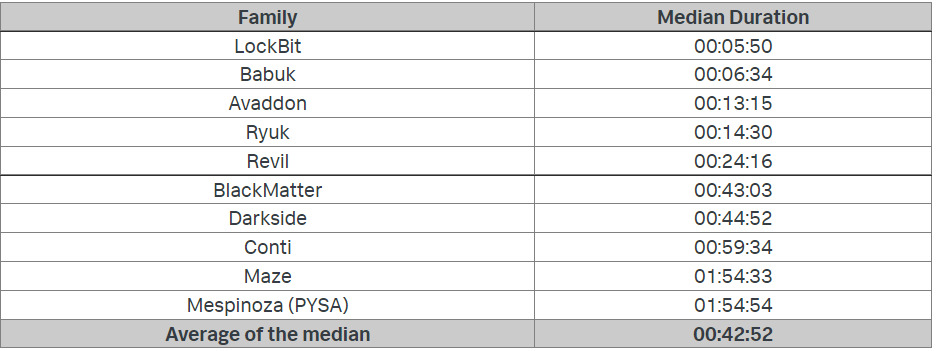
The research is also available in a white paper with more details. The team promised to publish more.
And finally the question comes up. What cybersecurity specialists can take from the research?
First of it’s the original hypothesis of the team that has basically led to this research. Is ransomware being too fast to stop it the very moment it gets on the system? As it turns out the chances are you actually have that rescue gap.
Tips: How to Avoid the Ransomware
But everyone knows for sure it’s always better to prevent the problem than deal with it. Once again I remind you the common tips to avoid getting ransomware infection:
- Use VPN services on public wifi networks. In case you use public wifi networks, always try to use a secure VPN connection. Especially use it when you do some sensitive transactions such as some banking payment;
- Use only trusted download sources. I think these days it should be an obvious thing. Only use those sites that have security and safety signs. Look to the browser address bar. There you should see “https” instead of “http” .Lock symbol or shield also indicates the safety of the resource. A special caution should be paid when you download anything on your phone. Use the Google Play Store or the Apple App Store when you need to download anything to your phone;
- Regularly check your programs and operating systems on new updates. When you have the latest version of a program or operating system it makes it harder for the cybercriminals to exploit them. It doesn’t take too much time to check for any new updates but certainly takes off many future problems;
 Is a real RED light for the different kinds of spyware
Is a real RED light for the different kinds of spyware
- Never use unknown USB sticks. This one tip is for very or too curious individuals. When you think nothing bad can happen if I see and what possibly bad can happen that’s where the trick hides. The point is you don’t know what is stored on that seemingly lost USB stick and it’s repeatedly better not to know. Some old saying goes “Less you know, the better you sleep”.
And the last but too obvious we just name them. Don’t go after suspicious links, don’t disclose your personal info where it can be unsafe, don’t open any suspicious email attachment. It’s just the tips but with common sense they make safety sense. So don’t just go into the unknown.