WannaCry ransomware is the first ransomware that attacked companies across the entire globe on May 12, 2017. It was aiming at thousands of computers in 150 countries. Among WannaCry targets were Honda, the University of Montreal, FedEx, and the National Health Services of England and Scotland. This ransomware also goes by the names like Wanna Decryptor, WannaCryptor and WannaCrypt. For injection, it uses the EternalBlue exploit, which allows threat actors to use a zero-day vulnerability to access the system.
Ransomware specifically targets Windows systems with legacy versions of the Server Message Block (SMB) protocol. Actually, WannaCry ransomware is a worm that spreads by exploiting vulnerabilities in Windows. Such a variant of a ransomware is particularly dangerous because it doesn’t need human involvement to spread.
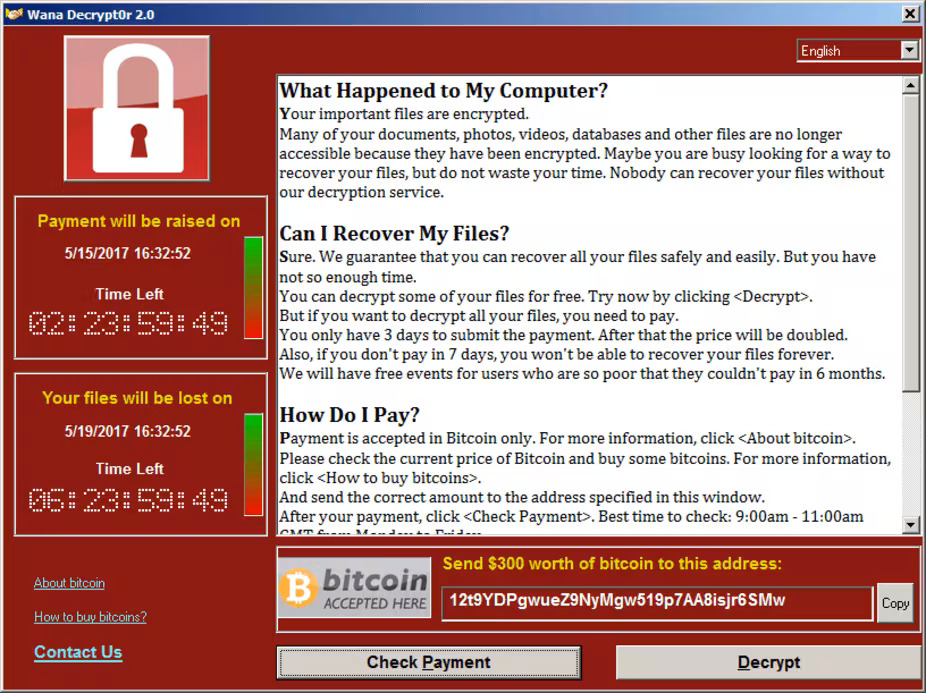
WannaCry ransomware note
Other common ransomware variants use phishing or other social engineering methods to spread. That means their software needs the direct involvement of a targeted person to spread and infect. Because of this feature, WannaCry is often referred to as a ransom worm or cryptoworm. But basically, WannaCry ransomware does what any other typical ransomware variants do, i.e. file ciphering and ransom demands. In May 2017 WannaCry demanded ransoms from $300 to $600 in Bitcoin. Victims should have paid this bill in three days, otherwise, ransomware promised to delete the files.
Who May Be Behind WannaCry ransomware
At its very beginning cybersecurity specialists attributed WannaCry ransomware activity to Lazarus Group. This advanced persistent threat (APT) group has a lot of ties that point to its relations with the North Korean government. In December 2017 the White House officially announced that the WannaCry attacks were the behalf of the North Korean government. The government of the accused country denied the accusation.
According to early reports WannaCry ransomware operators weren’t providing victims with decryption keys. That is likely an indication of premature release in May 2017. Operators obviously didn’t have at that time a fully operating system for decrypting victims’ files after ransom payments. Another important element of WannaCry ransomware attacks included the NSA EternalBlue exploit which received the identification of CVE-2017-0144.
Because many companies and organizations simply didn’t make the updates of their systems in time they fell victim to WannaCry ransomware.Days after ransomware began attacking massively, security researcher Marcus Hutchins (MalwareTech) found a kill switch that stopped WannaCry from further spreading.
How Much WannaCry Attacks Cost
The initial outbreak of WannaCry ransomware caused significant financial and operational damages to companies and organizations around the globe. However experts note that the said damages could have been worse because of WannaCry ransomware worm nature. Some general estimates show that the cost of damages amounted to hundreds of millions to companies and organizations around the world, but specialists from Symantec/Broadcom calculated that the actual damages possibly amounted to 4 billion dollars.
Nevertheless, during the first outbreak of the WannaCry ransomware attack in May 2017 more than 200,000 devices have been hit and still ransomware infects devices. After the first major outbreak of WannaCry ransomware U.S Congress prepared the Protecting Our Ability to Counter Hacking Act shortly after it in May 2017. It was proposed that any government’s software or hardware should be inspected by an independent organization. But the act was never passed.
The WannaCry ransomware was followed by an insurge in numbers of commercial ransomware attacks. It has been reported that in 2017 ransomware made up 39% from the general malware attacks incidents. Not only this but the sudden and strong outbreak of WannaCry ransomware raised important questions concerning cyber security of companies and organizations. Some roles in the IT security field have become more prominent due to their new and reimagined responsibilities.
Does WannaCry Still Present A Threat
Various exploits of Microsoft’s SMB protocol seem to be pretty popular with malware operators of all sorts and EternalBlue is no exception. In the June 2017 attack of NotPetya ransomware this exploit played the main role.
Another Russian-linked APT group that goes by the names Sofacy, APT28, Sednit or its more known name Fancy Bear. This cyberespionage group in 2017 attacked Wi-Fi networks in various European hotels using the EternalBlue exploit. In addition specialists note that the exploit has also been seen to be used by malicious cryptominers as one of their spreading mechanisms.
Although Microsoft has issued a patch for the exploited vulnerability systems that are still unpatched remain unprotected. And in fact specialists from Check Point Research observed a 53% increase of instances where companies or organizations were attacked by WannaCry.
The report was made about the first quarter of 2021. And in Q4 2020 and Q1 2021 specialists observed an increase of WannaCry attacks up to 57% .
WannaCry ransomware also set the tendency for cryptoworm and ransomworm concepts that were more than eagerly embraced by cybercriminals. Such code can easily spread via network endpoints, cloud networks and remote office services.
Basically ransom worms operators need only to find one entry point so that their malware could infect a whole network because it can quickly move across different devices and systems.
Another trend that was set by WannaCry ransomware is cybercriminals turning their attention to automated ransomware variants that can also have the ability to self learn. It’s a more prospective way of conducting ransomware attacks than operating traditional ransomware that need to be controlled via constant communication.
