VPN (Virtual Private Network) is a networking technology that supposes the addition of a virtual server to the connection path. Additionally, such connection features encryption, and by-design masks the user’s IP address. VPN requires a server through which the traffic passes and some controlling software. However, people often think of VPN as some program you install and use.
That’s true when we are talking about a VPN for individual clients. However, even with individuals software only connects the user to a remote server, where all the fun happens. In this post, we will try to figure out what VPN is and how it works. Also, we’d have a look at the types of VPN services, and the overall reasons to use VPN.
What is VPN and Why to Use It?
To make the story clear, it is better to start with why and then switch to how. When you connect to the Internet, you exchange data with your counterparts through the network. Theoretically, it is possible to intercept this data. If hackers compromise any node on the line that connects you with the one you’re communicating with, they can literally read whatever you send or receive. The threat is obvious – this information may result in different problems. Moreover, this data is not the only sensitive element. The information about your location, is contained in your device’s IP and some other accompanying identifiers. Thus, expectable threats came along with digital networking, which led to the emergence of various data protection methods, including VPN.
The one who legally gets information about your browsing is your ISP – Internet Service Provider. They see what websites you access, and they know where you live as well. At some point, it became clear that ISPs can exploit this access to your data. Nobody knows if that happens in any particular case, but it surely can happen, and it happened many times. Even considering the existence of HTTPS, the modern protocol of encrypted website connections, your Internet provider has enough data about your behavior on the Internet to sell it to advertisers who will use it to improve their ad targeting.
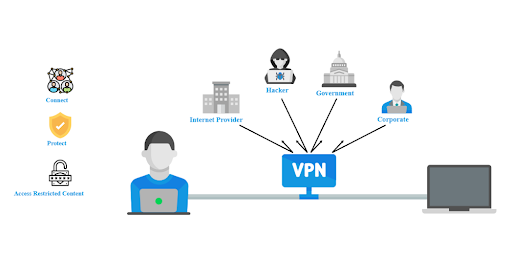
Simplified scheme of VPN connection
VPN server works as an encoding and cloaking device. You establish a connection with it, and nobody knows what sites you visit and which web applications you use because this gateway you are using encrypts all your traffic. Moreover, data transmitted from the server no longer carry information about your machine and its location. Read further to learn how the safety of such a connection is achieved.
How VPN works
When connecting to a VPN, the Secure Sockets Layer (SSL) traffic encryption protocol is used, where the connection begins with your browser and the server to which you are connecting exchange with the so-called public keys. The second element required for encryption – the private key – is not transmitted over the network. This technology is called asymmetric encryption. We can compare this to exchanging locks that close without a key. But then you can open them only with the keys possessed by each party. We will not go into details about how this is possible.
If you’re interested, read about trapdoor functions. The main thing is that if anyone intercepts such a message, there will be no point in it. It will take millions of years to brute-force a private key. The very process of establishing a secure connection takes less than a second, though. A single secret key is shared between the parties, and the linking switches to symmetric encryption, which works much faster than an asymmetric one.
SSL is also involved in the HTTPS secure communication protocol, but, as we have already said, this is not enough. Because the sites you visit – even with encryption of everything you do there – is already valuable information. For example, if you read the news on a particular site, advertisers can already decide which political ads to direct you to and which not. You visited one or another highly specialized online store? – the same thing. The ISPs will be happy to sell this data to third parties and let them know where you are in addition. That is why people use VPNs: to impose SSL protection on their entire browsing experience. The only thing your provider will see in this case is to which VPN server you decided to connect.
Virtual Private Network Benefits
So, let us list the undeniable benefits VPN brings to its users. These are three main features:
- Secure SSL connection. Interception of encrypted data becomes pointless. If you are not in a totalitarian state, where the VPN servers get blocked, you can gladly use VPN to hide your Internet history from your Internet provider.
- Hiding information about your machine and location. VPN gateway allots your traffic with the distinctive signs of the VPN server. The most trustworthy services remove the logs of your activity after a session, so no information is kept for any hacker to access. In worse cases, VPN providers undertake not to share this data. As for the worst case – skip to the last section of the current article.
- Assigning an IP of an arbitrary location. Since the resources you access (with a VPN) see you as someone from the place where the VPN server is (let’s say Italy, while you are in the USA,) VPN services thought up another feature they could start providing. By renting or buying servers all over the world to redirect traffic, they allow location spoofing by letting clients choose which country’s IP their connection would indicate. Location spoofing allows detouring barriers some countries might implement by controlling their national ISPs and also accessing content intended only for residents of certain countries or territories.
Must-have VPN features
If you want to choose a VPN, seek service with these functions, which are standard for decent VPNs nowadays.
- IP address encryption with location spoofing. Contrary to popular belief, VPN’s ability to spoof your location is an optional function. The essential one is the secure connection. Therefore, if you need a VPN for surfing the web from far-off places, make sure it is not some obsolete variant without such a feature.
- 2-factor authentication. The 2FA is a requirement to confirm your identity via another device, usually a phone. If you are going to use a VPN for serious data protection, make sure this feature is there. It will not allow anyone to steal your data if you need to leave your workplace unattended.
- Total protocol encryption. Although some VPNs provide decent traffic encryption, some extra data is exchanged between clients and websites. Search history and cookies should be encrypted as well. All VPN concealing might go to waste if it allowed any indirectly exposing data to be found beyond the session.
- Connection kill switch. A good VPN will kill the connection to the website if the VPN server or linkage with it goes down. Otherwise, all the efforts to secure your browsing would be spoiled when the browser and website switch to a direct connection.
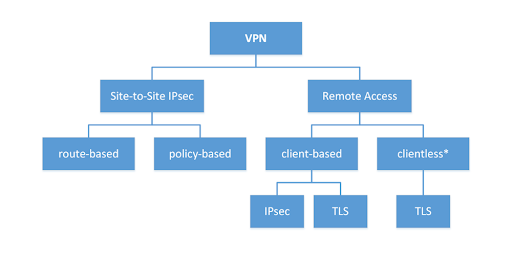
Types of VPN
Roughly, VPNs are for general and individual use. Strictly speaking, individual ones are VPN clients installed on specific devices (even a mobile phone, if you like) and manage the connections. Through such software, you can manage VPN settings, choose the quality of encryption, and select the country from which you want it to appear that you have accessed the Internet. The client itself may be a standalone software, but these programs are often built as browser extensions.
Next comes the VPN in the router or a special separate device. You can install one at home or in the office. Then everyone who connects to the Internet through this equipment will be protected by encryption.
- In addition, there are also corporate SSL VPNs for securely connecting endpoints to a server within the company, even on its intranet, as well as on the World Wide Web.
- Site-to-Site VPN is another variation of corporate traffic encryption used to safely exchange data and files within a company between different LANs (local area networks) within a unifying WAN (wide area network). As you can see, companies use VPNs rather protect data, not so much to fake IP addresses.
Are There Any Risks in Using Virtual Network?
To be honest, there are some. Using the virtual private network, you hide your data and information about yourself, but you trust it to another actor – the VPN server. So you have to admit that if it is an ISP you don’t trust, then you want to trust your VPN service provider. Otherwise, it is just a changing of guards; because every bit of data the Internet provider would benefit from becomes accessible to the VPN provider, who could be as quirky as an average hacker-spy and data dealer. However, if you need to hide your identity and location from the resource you are trying to access – you will hardly find a better tool than a VPN server.