Computer viruses is a very wide theme. Describing them all, without missing a thing in one article is pretty hard. So first, let’s start by defining the main computer virus types that are present nowadays.
The term “computer virus” nowadays serves as a global description of all malicious programs. But originally, viruses are… a type of malware. Over a decade ago, viruses were really widespread, so people used to call any malware case as “computer virus”. So do we – just not to confuse anyone.
How many different computer virus types are there?
Dozens. Some are still active, some became as rare as museum exhibits, and some disappeared because of non-actuality. Computer virus types such as worms, screenlockers and dialers. Let’s stop on the most actual ones – just to not make this article too big. And let’s start from the most dangerous one.
Ransomware. Say bye to your files
Ransomware is a type of malicious software which ciphers the files you have on your computer, and then asks you to pay the ransom for their decryption. Sly? Sure. Effective? Yep. Profitable? Much more than any other malware types. Decryption of files that were attacked by ransomware is oftentimes impossible. The ciphering algorithms used by these viruses are extremely tough, sometimes even military-grade ones. Hence, if this thing runs on your PC – you have nothing left but searching for possible backups or other sources of the lost files.
Starting from 2012, when Bitcoin showed its first significant growth, ransomware started growing, too. Cybercriminals searched a lot for a safe way to keep the stolen money. And cryptocurrencies are the best solution ever: anonymous, widespread and valuable as a storing unit. These days, ransomware nightmares both individuals and companies, asking for $500-$70 million ransom. And a lot of other fraudsters keep up after ransomware developers.
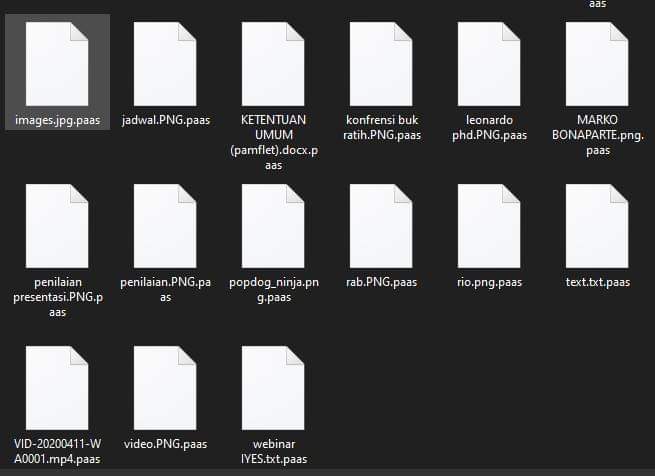
Files encrypted by Paas ransomware (Djvu family)
Coin miner viruses
Another thing that appeared after the cryptocurrency spread. Besides speculations on the crypto market or selling your goods/services for crypto, you can receive coins for a so-called mining. This is the operation of transaction block subscription – shortly put, helping with completing the blockchain. Fraudsters who spread and manage the coin miner viruses make use of someone’s hardware to conduct the mining.
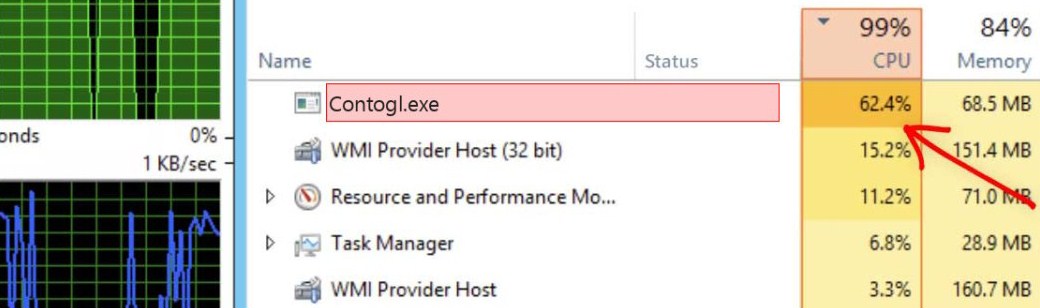
Coin miner viruses are very unpleasant for the user, but luckily, not for the files. Since it exploits your hardware, it is pretty easy to see 80+% of CPU/GPU consumption – and all of this is taken by a single process in a Task Manager. That is, exactly, one of the easiest malware to detect manually. A strangely-named process running in the background and consuming too much CPU will surely attract your attention. But it’s removal needs an anti-malware tool – pretty usual for something more serious than a joke batch script.
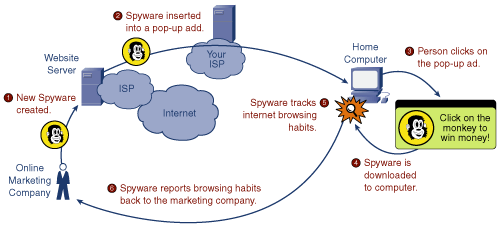
Spyware. Forget about the word “privacy”
Spyware is worth the attention, especially in case you don’t yet know what it is. These are malicious programs that can perform surveillance on the user and use it as a means to send data to a remote server. By the way, an unknown proportion of spyware infections start with a Facebook download. It’s fairly clear, though, that any kind of data gathering (unless encrypted) can result in criminal use of that data. If there’s no data-retention law in your country, you can consider yourself pretty safe.
Spyware may sometimes obtain a form of a legitimate app. In that case, it is called “spyware trojan” – since that malware acts just like the legendary horse dummy. That is likely the worst scenario, because such disguised malware is extremely hard to recognize and intercept. Besides selling the collected information to the third parties, crooks who manage spyware can easily use the obtained passwords/email addresses to log in your account and send spam, for example.
Stealer malware. Keep your files away!
Stealer malware is one of the most commonly spread types of malware, when it comes to attacks on individuals. And no, they don’t steal your stuff! Actually, it’s rather different. And it is also probably one of the least noticed because of its technical complexity. One of the most common copies of such malware is a text file which resembles an antivirus package (!). But let’s talk about what stealer malware does to your computer.
This kind of malware has a lot of things in common with spyware. But in contrast to it, stealer is aimed at certain data types. Spyware tries to collect everything it can reach, while stealer works with the things that are determined in its code. Usually, those are passwords, certain files that contain valuable information, or bank card information, for example.
Downloader virus
This kind of malware is used as an intermediary step – before injecting the main payload. When this thing appears in your system, it adjusts various system settings specifically to make it weaker. After that, the downloader connects to the command server, downloads and runs the full payload. Usual contents of the payload are coin miners, spyware and adware. Because of their extremal modifiability, it is often detected by antiviruses as “generic” malware – and thus ignored, because users think it is just a false detection.
Adware: get one more banner
Turning to the “light” malware. Instead of stealing your valuable information, adware usually just sends you ads for a whole range of programs. Sometimes, adware appears together with some “free” programs – both freeware or apps that were hacked and thus can be used without any payments. Being greedy always leads to problems, and this is just one of the examples.
Adware is highly customizable and can even change your browser preferences. Since they are installed by default, antivirus packages usually have to be patched against them. If you don’t want a specific program sending you ads, you have the chance to specify which ads you prefer to see. In short, adware is the kind of software that most people get, or are used to, already. However, if it shows up in a lot of unwanted places on your computer, you’ll have to keep an eye on it and remove it as soon as possible.
Exploit malware: isn’t that better?
Exploit is a sort of primary malware, which is used to make the system vulnerable to other malware injection. Nonetheless, in contrast to downloader viruses, it does not aim at system settings. This class of malware tries to find the vulnerabilities in the programs present in the system. Then, it tries to open it for exploitation – it will be very easy to inject malware into the system having such gates opened. Because of the obvious reasons, exploit viruses are generally used in attacks on corporations.
It refers to any way of exploiting programs that allows a hacker to take control over a computer in any way they want. With the ability to get any administrator privileges, they have the right to install a new operating system, change the startup procedure, and so on. Thus, they have control over the whole system. The exploits in programs can be detected by a number of ways; however, the most common methods are the software checks and signatures.
Backdoor. Computer virus that makes your computer a zombie
Have you ever heard about botnets? Ones that commence DDoS-attacks, hanging up tens of websites in a single evening? Or, possibly, you saw the bots which publish spam in the comments of something popular? All these things are the work of backdoor viruses. They are usually used to make your computer an obedient zombie, which will act as crooks say. This stealthy computer virus changes the networking setups and security settings, acting like a remote-access tool.
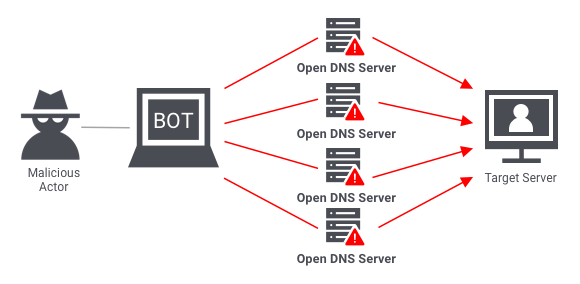
DDoS attack scheme
Thoughts on computer virus types
There are plenty of computer virus types. And there is no ability to prevent them manually, this or other way. Moreover, there is no need to do this job manually – you can just use anti-malware software. The best tool for this case is one that receives database updates as often as possible. Loaris Trojan Remover can boast of such a feature.
Cybersecurity is too important nowadays to ignore it. Each time you will think something like “that won’t touch me” – it will touch you as hard as it even can to. The more you know about malware – the less is the chance that you will be tricked to get it, or to escalate its abilities.