Credential stuffing is a type of attack where threat actors try to use previously stolen usernames and passwords on other victims’ accounts. This type of cyber attack is especially popular nowadays, because of the availability of stolen credentials on the Darknet. To successfully counteract this ever-growing threat you should know how it works and how to reduce its risks or even prevent it.
How Credential Stuffing Works
To do credential stuffing, threat actors simply put a pair of stolen credentials into an automated botnet which will try this pair on various sites at once. Rarely, crooks will do the same operation manually. Sometimes a stuffing attack causes a traffic surge – up to 180 times increase.
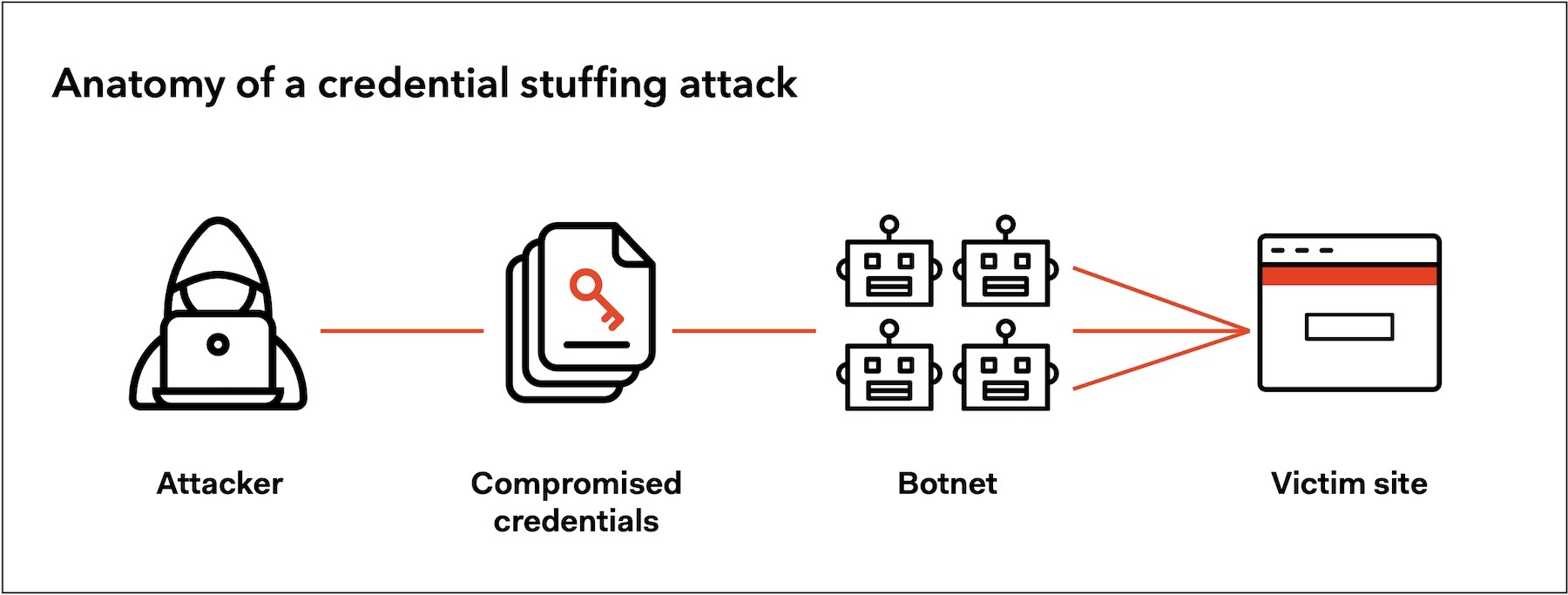
Once an automated botnet finds a match threat actors can do the next with the successfully compromised account:
- Institutional and corporate espionage/theft. One of the most devastating attacks on businesses and organizations. If the attack was successful, threat actors can now have access to various valuable data like addresses, social security numbers, credit card numbers and login credentials as well. As a result, they can sell it to whoever shows an interest;
- E-commerce fraud. Threat actors get access to other people’s accounts at some retailer websites to order high-value products for themselves or resell them later. If the victim attached a bank card to that account, all the payments will drain its balance;
- Selling access to compromised accounts. Threat actors steal accounts for major media streaming services like Netflix, Spotify, and Disney+ and sell them later on the Darknet.
Credential Stuffing Attack VS. Brute Force Attack
Often people tend to confuse the terms credential stuffing and brute force attack although they are related. Their similarity lies in the principle of work. In both cases, threat actors are trying to guess the victim’s username and password. Meanwhile, in brute force attacks crooks don’t know the actual password or username, they need to guess them. For that purpose, they use the “dictionaries” – large databases of popular passwords. The more actual passwords the dictionary contains – the more it costs to purchase.
To protect yourself against brute force attacks you can limit the number of possible failed login attempts, enable CAPTCHA or require stronger passwords. Still, strong passwords won’t help if threat actors already know it. In case you have your password leaked, create new ones that don’t resemble your previous one in any way. Crooks know that many users tend to create new ones that has things in common with their earlier passwords.
How Serious Credential Stuffing Attack Can Be
According to the Securities and Exchange Commission credential stuffing attacks have been on the rise since people started to have more accounts. The other proof of credentials stuffing popularity is the appearance of a so-called Pemilanc list. It contains over 111 million records of usernames and passwords. Among the biggest and most serious credential stuffing incidents is the JPMorgan Chase hack in 2014. Threat actors managed to get access to a cache of a billion stolen usernames and passwords. Another example of corporate-scale credential stuffing happened with three eBay employees. Threat actors gained access to the company’s network using the credentials of those staff members. The attackers had access for an astonishing 229 days.
The Cost Of Stuffing Incidents For Companies And Organizations
Despite their seriousness, credential stuffing attacks generally have a low success rate. The average effective rate of this operation is 1-3%. Although they have such a low success rate, credential stuffing attacks can have a much bigger impact on their targets. According to the Ponemon Institute’s Cost of Credential Stuffing report, companies lose on average 6 millions anually because of stuffing.
The reported cost of such losses includes the loss of customers, application downtime, and increased IT costs. Aside from these costs, credentials stuffing attacks can also lead to fines under GDPR regulation. GDPR stands for the standards of customer data protection. If a company keeps it without proper protection, GDPR can impose heavy fines. And don’t forget about sues from upset customers – they’d likely want to get compensation as well.
How To Prevent Stuffing Attack
To prevent credential stuffing attacks both users and companies should take precautions. It’s important to say that their separate application will have minimal to no effect. All these tips have their peak efficiency once applied jointly.
- Set regular monitoring for leaked credentials. A service provider can use specific solutions that will help users to scan their login credentials and see if there’s been a compromise. Such scanning solutions compare current credentials with ones published in the Darknet. If the match is present, app notifies the user.
Not only service providers can use scanners for leaked credentials but ordinary users can enter their credentials on website like HaveIBeenPwned.com to see if they have been somewhere compromised; - Enable multi-factor authentication (MFA). In addition to having one password to log in with two-factor authentication (2FA) or multi-factor authentication (MFA) you will need to go through additional steps of verification like one-time code, pre-registered security question or even enter your biometrics (facial recognition, fingerprint) before getting access to your account;
- Limit failed login attempts. Service providers can set a limit on how many times users are able to try to log in. For example, financial institutions are very strict on this matter; usually you can only try from three to five times to log in after that the account a user tries to access gets deactivated.
Of course, not every service needs such a strict verification method but it will be useful where the attempts to get unauthorized access are much higher than generally; - Enable web application firewall (WAF). WAF was designed to prevent all data breaches that can occur via the web. It can’t necessarily stop credential stuffing taking place but it will detect an anomaly high level of attempts to log in that usually comes when threat actors use the botnet for credential stuffing;
- Create unique passwords for each service. The easiest and seems to be the most reliable solution against credential stuffing attacks. All you need to do is to create a complex and strong password that won’t be easily guessed by anyone unauthorized.
Of course, it can be difficult to create and to remember all the passwords if there are fifty or even hundreds of them.
As a solution for this you can use specially created password managers that not only will securely store all your passwords but also will create complex and strong ones.