A password is arguably one of the most underrated security tools nowadays. They are so ancient as a phenomenon, seen in so many applications and services, that understandably, people who use them for protection don’t know how problematic it is to break a strong password. Login credentials are a Helm’s Deep of any targeted system. Theoretically, crooks can crack them with brute force, but it takes millions of years to break a good password. In this post, we shall cover the related security issues and advise a little on password management.
How to Come Up With a Strong Password?
Users tend to underestimate passwords imagining hackers just like they are depicted in movies and computer games. Access denied? No problem! Initiate an “ice-breaker”. But that is an unrealistic scenario. Password breaking via brute-force attack is a rare procedure, rather theoretical than practical. But we shall touch on that later. The password strength must define whether breaking it with a blunt variant guessing is realistic.
- Don’t use the same password on different, let alone all accounts. If criminals lay their hands on one of your passes, make no mistake, they will take it as a possible base for your other passwords. This tip does not relate to the strength of the particular combination, but having different passwords is a critical aspect of data protection in general.
- Use letters of upper and lower case, digits, and special symbols. Following this rule will make your password virtually unbreakable. It will still be possible to brute-force it, but this will take some time. Billions of years, not less.
- Avoid using data that means something to you. Birthdays, names of your relatives, slogans, and idioms – none of these are decent to be a base for your password. Hacking attempts nowadays are often parts of spear attacks. It means hackers usually know something about their victim. They ordinary to pick the password not randomly but by developing variants of what could probably become one.
- Do not use keyboard combinations like “zxcvb,” “qwerty,” or “poiupoiu”. They only seem random, but they are pretty predictable consecutive pressings on neighboring keys. Everyone can quickly strike them with one hand. Codebreakers have card files of such combinations loaded in their password-picking software.
- Log out if you leave your workplace. Do not forget to log out if you have to use someone else’s computer to log into your accounts. In case you forgot to log out, you can always use the remote logout feature available in most online services’ settings.
- Use two-factor authentication. You must confirm your identity via another device when you enter your credentials. Google has made 2FA obligatory, and so should you. The current feature does not make your password stronger, but it significantly strengthens this chain link.
Don’ts in Managing Passwords
Theoretically, hackers might perform a brute-force attack on your password. But whether they succeed depends on their quality. The temporal difference between cracking a weak password and a strong one exceeds the current lifetime of our universe. That means a “0000” will be picked in less than a second. Meanwhile, a strong password will keep the same code-breaking program busy for quadrillions of years. The following points are the things you should avoid to make brute-force attacks a little bit costly in terms of time required and passwords unobtainable.
- Don’t stick to the same passwords for too long! Change them! This requirement is so important that most services automatize meeting it. However, corporate security might need to schedule password changes by the employees.
- Do not log into your accounts on questionable devices and wireless networks. Spyware and keyloggers, which record keystrokes, are a concern here. In the case of wireless networks and mobile devices, it is even more dangerous. A man-in-the-middle attack is a hack that places a cyber thief right between you and the Internet, most likely via special software installed onto the wifi router, to steal your credentials.
- Do not share your passwords with anyone. You don’t. Just as simple as that.
- Do not leave your passwords written where other people would find them. People are often vainglorious when it is unjustified but rarely cautious enough regarding data protection and Internet security. However, crooks need our data for pretty mercantile reasons. Therefore, the thought that we are not interesting to anyone should not be a reason for carelessness.
How do hackers beat or bypass passwords?
Phishing attacks
Phishing is one of the most effective ways to get in possession of the victim’s credentials. These attacks can do without malware; the only thing required for a successful phishing attack is social engineering and spoofed websites and emails. The crooks impersonate a trustworthy company and claim that the user either needs something to change an account password, receive a pending delivery, or participate in a survey. There are many ways to deceive an unprepared person. The thieves casually ask the victim to enter a password along the way. They present it as a necessary and purely technical procedure. In fact, for the sake of this moment, everything have started. Since the form the victim fills looks like an official company page, the scammers are trying to impersonate it. An inexperienced user most likely delivers the precious password to the crooks.
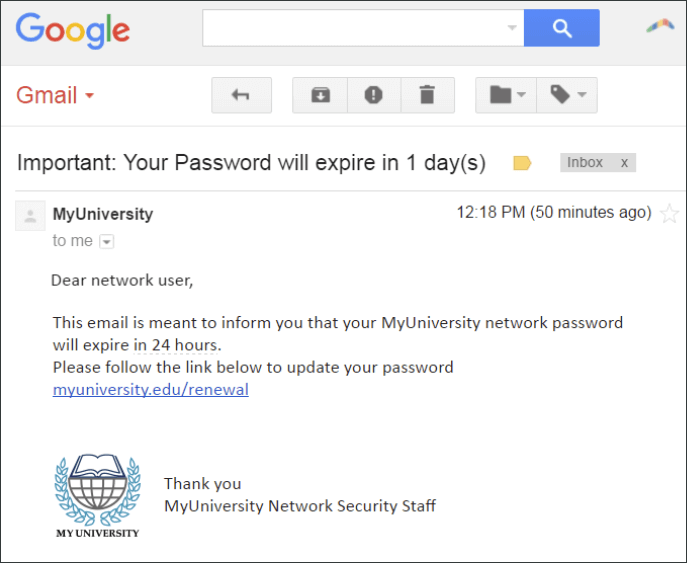
A typical password-requesting phishing email with a spoofed letterhead.
The best weapon against phishing is vigilance. Always examine the website link and email address of the sender. Also, know that no company will ever ask its clients via email to enter their passwords.
If cyber thieves manage to install form-grabbing software onto the victim’s system, they will be able to receive the data from the filled sign-in forms unbeknownst to the victim. Such software is usually downloaded by Trojans, or it may be their initial payload. As for the origin of these programs, the story is old: questionable email attachments, unchecked Internet links, untrustworthy installations, and peer-to-peer network downloads.
 Is a real RED light for the different kinds of spyware
Is a real RED light for the different kinds of spyware
Should malware like the form-grabber plant itself in your system, be sure that a decent antivirus solution like Loaris Trojan Remover will kill a form-grabbing intruder in no time.
Brute Force Breaking
Trying to pick a password with brute force implies exhaustive trying of all possible character combinations until the right one is guessed. Frankly speaking, brute force is only effective against weak passwords. Not to squander the capacities of modern computers and yet somehow succeed, hackers have modified brute-force procedures inventing dictionary attacks.

This table shows the effectiveness of strong passwords against brute-force hacking.
Dictionary Attack
A dictionary attack uses the automatized codebreaking employed in brute-force attacks sophisticating it with an algorithm that defines the words that fit the role of a possible password basis. The breaker does not try all possible combinations but the variations deriving from the dictionary.
The logic behind dictionary attacks is that humans rarely think of random combinations but rather base their secret words on existing names or terms. Although it is counterintuitive, statistics show that dictionary attacks are much more successful.
If the hackers know the words mean for their particular victim, making it a spear dictionary attack, the password can be hacked even faster.
Keylogger Malware
Keyloggers are malware whose purpose is to record keystrokes. The keylogger works on the victim machine and sends the obtained data to the hackers. Keyloggers installed on public machines where people are more likely to input passwords manually pose even more risk.
There are three main ways to protect yourself against keyloggers:
- Do not let hackers infect your system with it (precautions mentioned above).
- Use a virtual keyboard. It might help against most keyloggers.
- Install security software. Loaris Trojan Remover gets its malware databases regularly updated. The keylogger will be removed as soon as it penetrates your system.
Password Stealer Malware
Password stealers are harmful programs that can extract credentials from applications (mostly, web browsers) that store them on the device, not the cloud. Attacks involving stealers are becoming obsolete, but some programs are still exposed to this type of malware. The best remedy against a stealer infection is an antivirus program.
Leakages
It has already been said that passwords stored in the cloud are safe in most cases. But the cloud is just a word. We are talking about a server that is also subject to attacks. In addition, information leakage can occur due to someone’s evil will or accident. In short, from this, of course, no one is protected. If you are not the target of an attack, then be calm. Upon learning of the leak (and if we are talking about Facebook or Google, they will trumpet about it), immediately change the password to a strong one.
Conclusion
The tips in this article are a basis for decent data protection. An anti-malware solution installed and running – is its second part. Phishing attacks require vigilance and leakages – news monitoring. But at the end of the day, the main thing is to be serious about cybersecurity in general, with passwords being its crucial component.