There are a lot of branches under the term “cybersecurity”. Computer network security, information security, security of the single computer – all these branches of cybersecurity are very large. And all of them are essential for understanding if you use PC. Online security, an integral part of this enormously actual study, often leaves behind the scene. In this article, you will read the key rules of proper usage of web resources, as well as some tricks that can help you to avoid malware injection.
It is strange that the main source of hazard that gave a significant push for cybersecurity as a science remains behind the scene. Of course, there is a huge range of worldwide-accepted solutions that act as embedded antiviruses. But the observant user who knows enough about web security can manually find a lot of potential breaches. The majority of these vulnerabilities are based on the human factor. Carelessness, which often goes close to foolishness, and simple lack of basic knowledge about online security – they look like easy-to-counteract, but the statistic reveals other facts.
What is online security?
Usually, scientists use this term to describe the rules that prevent any bad finals from browsing the Web. These rules help to make sure that sensitive information you use on the Internet will not leak anywhere. The result may be reached with the solutions for browsers, as well as with regular antivirus tools.
In specific cases, online security terms may describe a large pack of measures that aim at minimizing the possibility of information theft data leaks, or malware injection. The difference between the former and the latter is in the depth of practices applied for reaching the target. The first term is more descriptional, the second includes practical usage cases. Besides antiviruses and modern browsers, online security requires much more technical methods as well as human resources.
Looking at the roots of online security
Which hazards hide online? Such a question will be hard to answer even in the dissertation. So, let’s categorize the main hazard outlets that must be closed by online security:
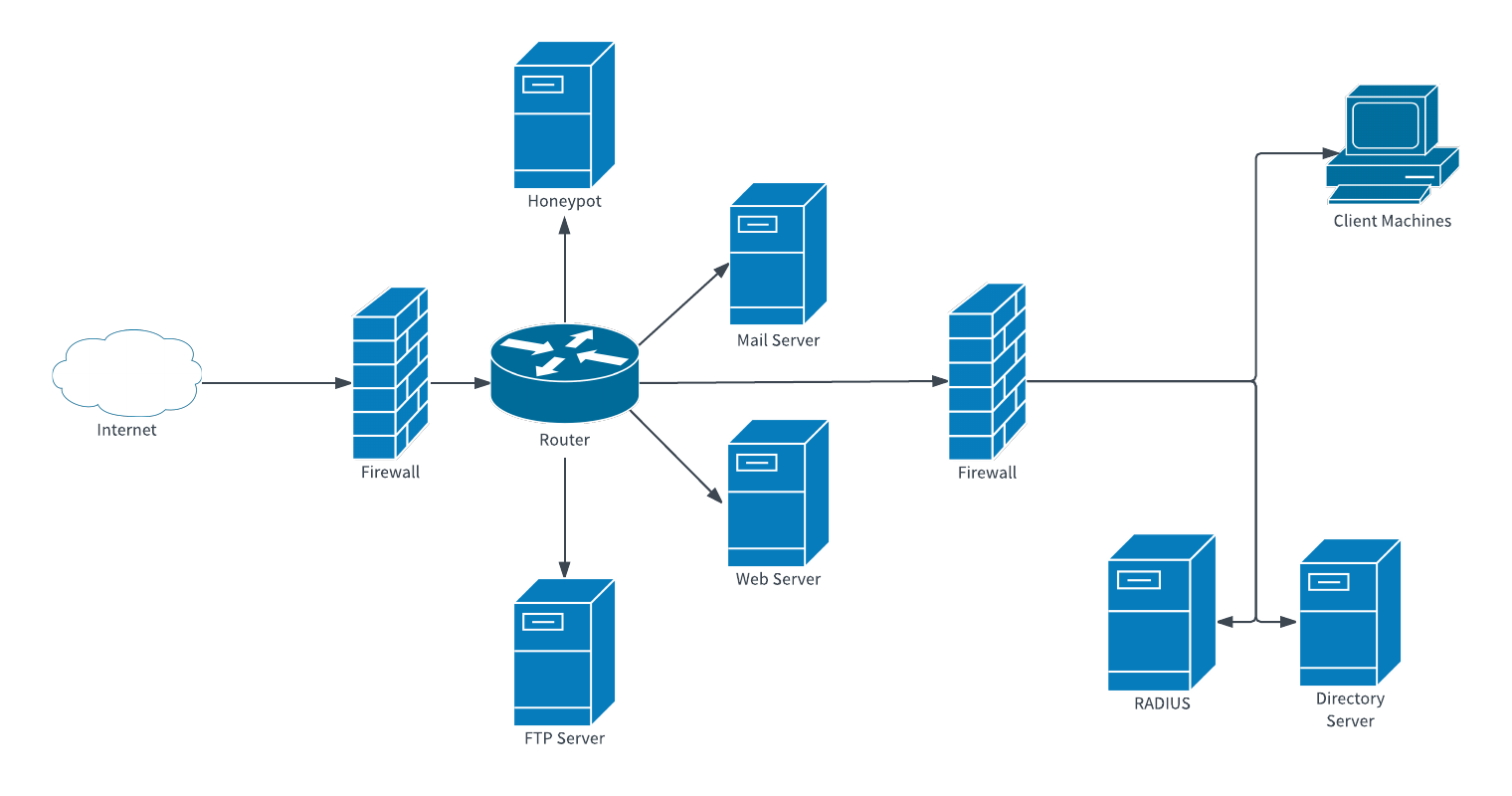
Fake websites
Sites that mimic the file-sharing resources. Originally, websites of this type are often used for sharing the content for web pirates. Those are cracked programs/games, cam-ripped films, or any other data that should be paid for. Fake file-sharing websites are offering to download anything you will type into the search bar. They will give you “relevant” results even to absurd search inquiries. Under the downloading link, you will find a backdoor, adware or some other unpleasant thing.
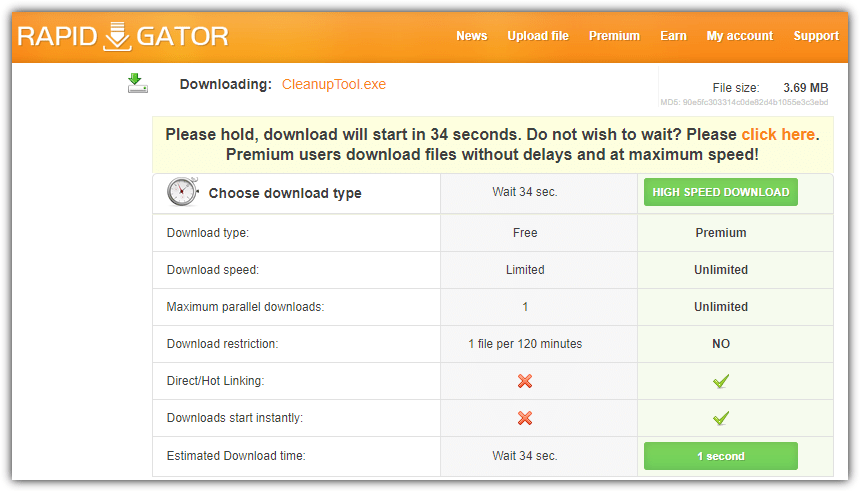
Malvertising
Everyone has seen the advertisements with dubious content at least once. “You won the lottery”, “We have a gift for you” or “You are the 100000 visitor of our website, take your prize!” – all of them are also blinking awfully and painted in dangerously bright colours. It looks obvious that you will get nothing but malware, or a redirect to another page. However, there are enough users who still click on it.
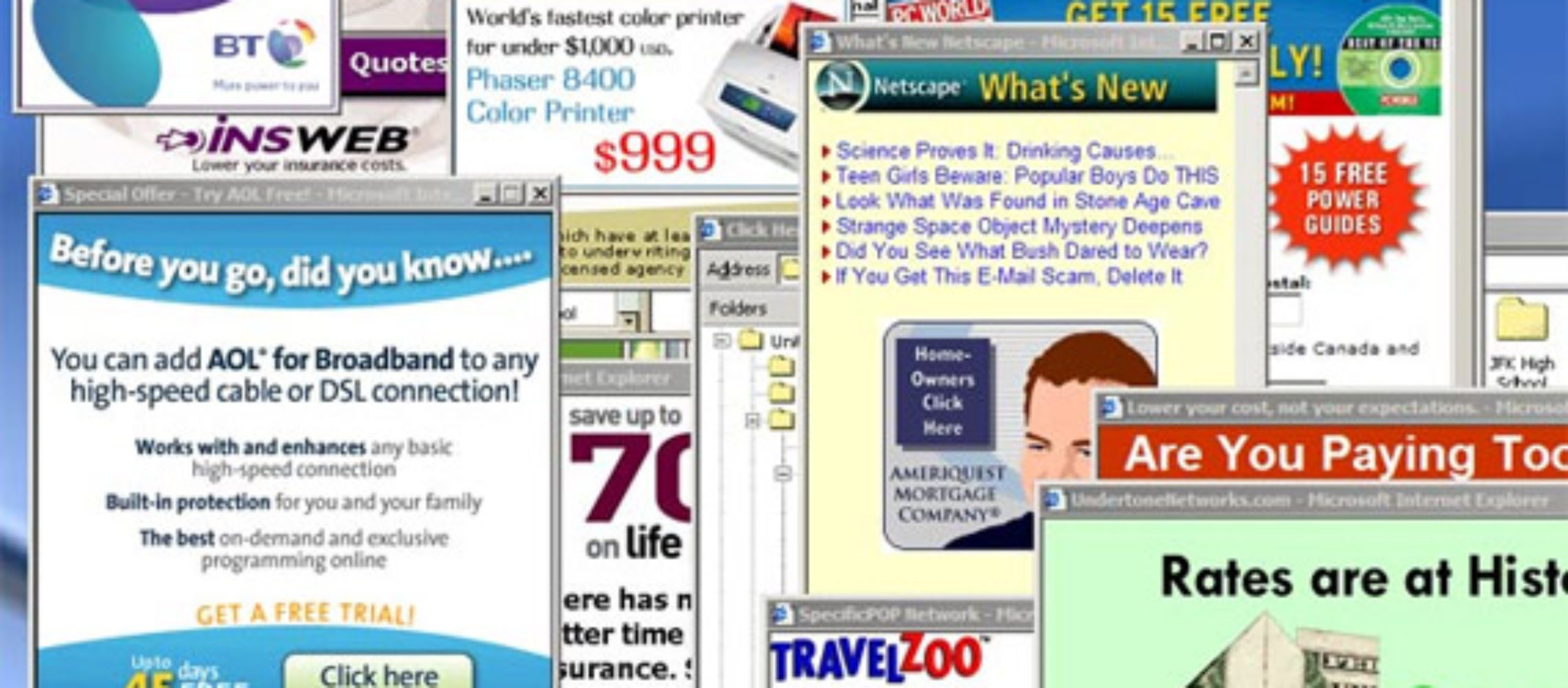
Phishing websites
Did you ever receive a message that pretends to be a Google giveaway? Or an email that says your bank has blocked your account? Both of them are classic examples of a phishing scams. Sites that mimic legit pages are quite easy to create. Some time ago, that was hope that HTTPS implementation will save folks from this mess. However, statistic says that 75% of phishing pages nowadays have HTTPS certificates. Hence, only your attentiveness will save your personal details and costs from leaking. Check the site without haste; review the email sender’s address. Most often, you will see the sign that will surely point at a fraud attempt.
Abandoned or compromised sites
There are two subtypes of this threat. First one is a common website, which is compromised and controlled by cybercriminals. Any part of the content located on this website can be malicious. Such pages are getting reported quite quickly, and the majority of anti-malware programs begin to block them in a week or two. The other type of abandoned website is a forum or chat that has no active moderation. Users are free to share any files, so the chance that someone maleficent will post a malicious file under the guise of the app you asked for is very high.
Website that is no longer supported
Websites that were reported for dubious activity
Unlike the hacked pages, the ones that were reported for dubious activity are not hacked. All such activity is done with the allowance (or even direct control) of website maintainers. Some of the web browsers may display the notification about the suspicious activity on this page, but antivirus software will likely ignore this site.
Doorway websites
Doorways are often used by adware or malvertisiers to redirect the user who clicked on the promotion. Such sites have no content – only links to other websites. About 5-8 years ago users who were employed in search engine optimization used doorways to pump the website they wanted to optimize. Nowadays, Google, as well as all other search engines, are blocking all attempts to move the site higher in a search index via doorways. So, it is easy to make the conclusion that if you see a web page full of links, you likely have malware on your PC.
Most of the issues you see above cannot be fixed only by using the antivirus program or installation of the latest version of the browser you use. It is needed to know the key principles of online security to prevent the well-hidden attempts of attack. As it was mentioned, to provide the complete online security, you need to implement an enormously huge amount of solutions. It will take a lot of pages of text to talk about all possible ways of creating a perfect online security shield, so let’s figure out the main (and the easiest) moments.
Tips for better online security
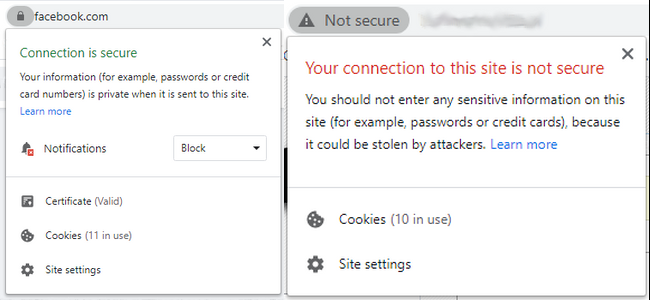
Always check the website certificate
When you are not sure about the link you followed, check if the website has the HTTPS certificate. This thing can be obtained quite easily, however, counterfeit websites that try to mimic well-known resources, like LinkedIn or Facebook, will surely be denied in the certification.
Avoid clicking on the advertisements without the Google Ads/AdChoices label
Both of the mentioned advertisement services (and more others) review the organizations who order the ads, as well as the content which will be displayed after following this ad. Hence, the chance that you will get viruses on your computer is very low. Also, due to the advertising standards, companies are not able to show you the ads that are covering the part of the content on the website, or even covering the full screen.
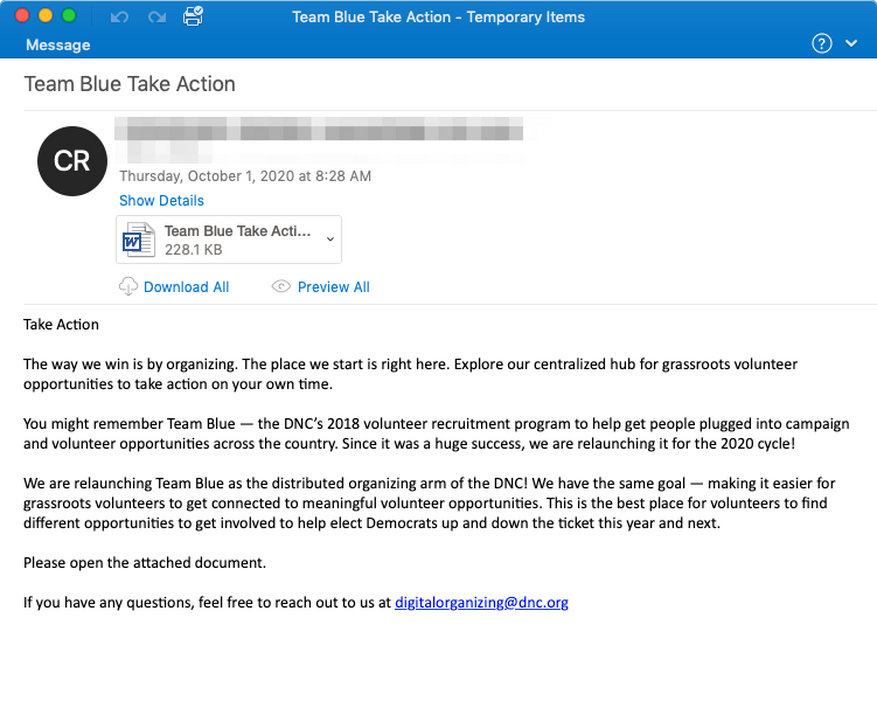
Do not follow the links that are found on the untrustworthy websites/sent from unknown email addresses.
Only the sender knows what will happen after following the link he sent. It is very risky to open such a link, especially if the sender states that this reference leads to the downloading. The risks are getting even bigger when we have a look at actual statistics1 of the ways of ransomware injection – the biggest share is after the email spam, that contains different links or files that have trojan virus inside. As the result of the activity of this trojan ransomware is injected and launched.
Afterword
Following these simple guides will decrease the chance of getting infected while browsing the web. Of course, making your computer invincible to any type of virus is a much harder task, but closing the main malware source will surely make you less nervous.
Another trick, that may be useful for prevention of any type of computer hazards is making use of the security tools two times a week allows you to crop the malware activity on the initial stage, minimizing the risk of being infected with something much more serious. Loaris Trojan Remover is an effective tool with an affordable price that will surely deal with all possible viruses you have.
 Is a real RED light for the different kinds of spyware
Is a real RED light for the different kinds of spyware
- Statistics about the ransomware activity through the 2020