We are used to the situation that you can get Internet access wherever you want. You will likely be unpleasantly surprised when the hotel where you have a night has no Wi-Fi network. Free Wi-Fi can be met even in a little café, or in the public park across the road. But there is an invisible danger, that is actual for every public Wi-Fi network. Let me explain to you, which hazards do I mean and how to decrease the related risks.
How can Wi-Fi be dangerous?
Your own home wireless network access point has a lot of differences with public Wi-Fi networks. And I meant not only technical details but also the external factors that surround hotspots through their usage. Saying short, technical details influence is minimal – you can easily meet the network in a restaurant that has the same technical aspects as your home Wi-Fi does. So, let’s check out which factors can lead to unpleasant consequences for your data and privacy.
Encrypting mechanism
Every Wi-Fi router provides the ability to choose the security mechanism for the new network. However, as there is no display on the router, it is equated with the periphery devices. To set it up, you need to connect to the just-created network with your computer or laptop. The interface of a web setup application is not very user-friendly, especially on some advanced firmware variants. Hence, the majority of users just plug the router cable into the power outlet, insert the Internet cable in it, and then start the Wi-Fi usage. When the user finally gets to the settings, it will rather choose the path of least resistance. When the user has no experience, it will likely choose the WEP encryption, simply because it contains way less settings than WPA. But what is the problem with WEP?
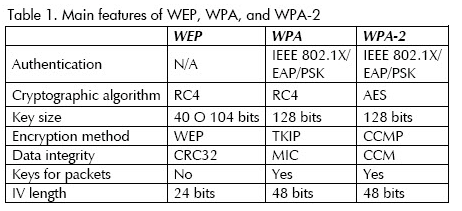
WEP Problems
First, let’s figure out why traffic encryption is a must-have. Every time when you get a message or watch a video on YouTube, your device swaps the data packets with the server. A third party can intercept and read by anyone who has the special software. Such an attack is called Man-in-the-Middle (MitM), and it sees its primary application for stealing personal data. MitM can show hackers your credentials, including banking information, chat messages, and so on. Further, crooks will likely sell it on the Darknet, and other crooks who purchase it will use this information for their dirty doings. Encryption makes the traffic impossible to read by the third party, so all mentioned problems will be much harder (or even impossible) to perform.
Wired Equivalent Privacy (WEP) uses the 40-bit encryption key, and that’s extremally low for modern needs. Because of some features of the encryption mechanism that Wi-Fi routers use, it is sometimes even easier to crack. WPA, which was presented as a successor1 of the WEP, uses 128-bit (or even 256-bit, if we are talking about WPA-3) keys, which are likely impossible to hack.
So, after these spatial reasonings, we can make a conclusion, that 1 man with the proper software on his laptop is enough to make your private conversations not so private. Sure, there are enough other ways to get into client-server communication, but they require way more effort as well. And WPA protection, together with the use of HTTPS-protected websites, makes the hackers’ chances close to zero.
Creating a fake Wi-Fi network
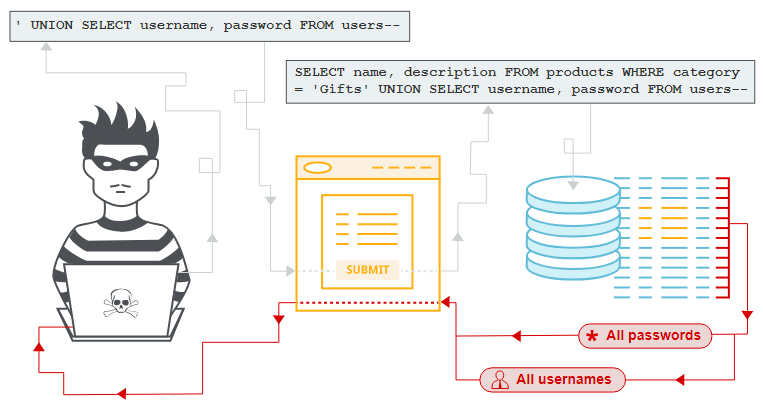
There is also a more developed variant of the classic MitM attack. Cybercriminals create an access point that is placed very close to the local restaurant, and name it as close to the name of the Wi-Fi network of this restaurant as possible. Such hotspot may be named as “Starbucks_”, while the original one has no underscore in its name (simply “Starbucks”). After the network is established, the hunt begins. People connect to this network without any suspicion, and then start browsing the network in their usual way. Because this network is controlled by maleficents, they can check all data packets without any trouble. Besides traffic control, they can force the victims’ browsers to open the phishing websites in spite of the pages they are opening2.

Visualization on how MitM works
Rules of secure usage of public Wi-Fi
Prefer to use the secured networks. This solution is obvious, but even WEP encryption is better than no encryption at all. Of course, you can get into a situation when there are no networks with encryption in the range, but the risk may be too big to make such a reckless action.
Do not share important information through public hotspots. When the circumstances force you to use unprotected Wi-Fi, try to minimize the risks. Do not log in your accounts, avoid using the banking app, and do not send any files that must not be in public access.
Always check the proper SSID of the Wi-Fi network you are going to use. Usually, all cafes, restaurants or hotels which offer the wireless Internet access point, also provide the network name (SSID) somewhere at the reception, or in the room. Check these places or ask the staff for the correct information. Most of the MitM cases these days rely upon fake access points that mimic the SSID of the genuine one.
Use virtual private networks (VPN). This trick allows you to forget about the first type of MitM attack (when the network is not controlled by cybercriminals). Nowadays, VPN may be embedded in your anti-malware program, so you can set it up without any additional downloads. However, if you will connect to the counterfeited hotspot, VPN will not be able to protect your data.
- WPA security mechanism description
- Detailed article about the internet security