Smurf attack is a specific type of distributed denial of service attack (DDoS). It supposes flooding a target server with spoofed IP and ICMP packets. As a result, the target server becomes inaccessible. The name comes from DDoS.Smurf malware tool, which was widely used in the 1990s. A small ICMP packet generated by a malicious tool can cause considerable damage to a victim’s system. More broadly, the attacks are named after the cartoon characters Smurfs because of their ability to take down larger enemies by working together.
History of Smurf Attacks
The smurf attack was originally code written by the famous hacker Dan Moshuk, also known as TFreak. The first mentions of this attack date back to 1998 and initially targeted the University of Minnesota. The attack caused a cyber traffic jam that affected Minnesota’s statewide Internet Service Provider (ISP) regional network. In addition, it shut down computers across the state, slowing down networks and contributing to data loss.
How Does It Work?
Smurf attacks are similar to Denial of Service (DoS) attacks, called ping floods, because they are carried out by flooding the victim’s computer with ICMP echo requests. The attack takes place in several stages:
- Finding the target’s IP address. The attacker identifies the target victim’s IP address.
- Creating a spoofed data packet. To make a fake data packet or ICMP echo request, the Smurf malware is used, the source address of which is equal to the victim’s real IP address.
- Sending ICMP echo requests. An attacker deploys ICMP echo requests on the victim network, causing all connected devices on the network to respond to the echo requests with ICMP echo reply packets.
- ICMP response overflow. The victim receives a stream of ICMP Echo Reply packets, causing a denial of service for legitimate traffic.
- Victim Server Overload. If enough ICMP response packets are forwarded, the victim server overloads and becomes inoperable for some time.
Define Smurf Attack
An additional component of smurf attacks that can increase their potential damage is smurf amplifiers. The amplification factor correlates with the number of hosts on the victim’s broadcast IP network. Thus, a broadcast IP network with 300 hosts will give 300 responses to each spoofed ICMP echo request.
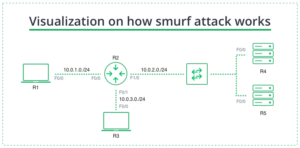
Visualization on how smurf attack works
This allows a low-bandwidth attacker to successfully disable a victim system, even if that system has a much higher bandwidth. Such amplifiers can be deployed as long as the attacker maintains the connection and the amplifiers broadcast ICMP traffic.
Types of Smurf Attacks
Smurfs’ attacks are usually classified as basic and advanced. The only difference in attack type is the attack’s degree.
Basic Smurf Attack:
A basic smurf attack occurs when an attacker fills a target network with endless packets of ICMP echo requests. The packets include a source address set to the network’s broadcast address, through which all devices on the network that receive the request issue a response, thereby causing a huge amount of traffic that will eventually cause the system to shut down.
Advanced Smurf Attack:
This attack is similar to a basic attack. However, echo requests can configure sources to respond to additional third-party victims. This allows attackers to target multiple victims simultaneously, slowing down more extensive networks and targeting large groups of victims and large network sections.
Differences Between DDoS attacks and Smurf Attacks
DDoS attacks limit victims’ access to their network by flooding it with fake information requests. A Smurf attack is also a DDoS attack that incapacitates the victim’s network. However, unlike a DDoS attack, it exploits IP and ICMP vulnerabilities. These vulnerabilities are the main difference between Smurf attacks, thus increasing the potential damage.
Differences between Fraggle Attacks and Smurf Attacks
Like Smurf, Fraggle is a form of DDoS attack. The difference is that while the Smurf attack uses spoofed ICMP packets, the Fraggle attack uses spoofed User Datagram Protocol (UDP) traffic. Everything else about these attacks is similar.
Consequences of a Smurf Attack
Although the primary purpose of a Smurf attack is to make the victim’s system unavailable for some time (a few hours or even days), it can also be the first step toward more dangerous attacks, such as theft of sensitive information or identity theft. In any case, there are necessary consequences of a smurf attack:
- Loss of revenue: if a company’s server is down for hours or days, it stops business operations, resulting in a loss of income and frustrated customers.
- Data Theft: Hackers can gain unauthorized access to data on a victim’s host server during an attack.
- Reputation damage: If your customer’s data can be leaked after an attack, it can permanently undermine their trust and loyalty to your organization.
Protection from Smurf Attacks
Fortunately, installing protection against smurf attacks is not difficult. The features demanded by scammers have long been known, and they can be easily countered with little or no loss of functionality. Although it is impossible to avoid a DDoS attack completely, the efficiency of such attacks is reduced to 1 request per attacking computer, regardless of the number of computers in the network.
- Disable IP broadcasting. The inability to send replies to your network makes such an attack impossible. However, this can be a problem for some features, such as FTP/SFTP connections. This setting must be done on the router.
- Deny ICMP responses received. This function will filter ICMP response packets commonly used in smurf attacks. Meanwhile, hackers are not required to use this type of packet, so it is not an ideal solution.
- Set up a firewall to filter pings from the outside. This solution can cause minimal problems in your workflow. Not being able to ping your server from the outside stops packets from being routed (they don’t get anywhere) and probably stops cybercriminals from trying to hack into your domain controller.
In addition, investing in an anti-virus and anti-malware solution to protect your firewalls add an extra layer of protection to your network.