STOP/Djvu ransomware family is individuals’ most widespread ransomware family. This malware type is infamous for its ability to lock the files and then ask you to pay a large sum of money to get them back. Appearing in December 2017, it is one of the oldest ransomware families among the ones that are running these days.
STOP/Djvu family has a share of almost 75% of all ransomware detections when we talk about individuals. Such a “success” results from amazing cooperation with other malware creators and good awareness about all possible malware spreading ways. It is unclear how much these guys earn, but the gross losses from ransomware activity exceeded $11 billion in 2021.1 They will likely grow in the following years – and Djvu will be in touch. The FBI is interested in capturing at least one of their top managers.
What is a STOP/Djvu Ransomware?
Being successful usually means having something unique in your product. But the core of the ransomware they produce brings nothing that can give such a big spread. Key things that make Djvu virus so successful are the aforementioned spreading ways, and a unique repacking mechanism, that allows this malware to stay undetected for a long time.
Like most other ransomware families, STOP/Djvu uses AES-256 or RSA-1024 encryption methods. Sometimes they combine them, but there is no need for such a strong cipher. Even AES-256 is enough to prevent any decryption with a brute force. And there is no way to get the key – in 95% of cases, it is kept on the command server and sent with asymmetric encryption. That means there is no way to get it without paying the ransom. Unfortunately, even quantum computers cannot decrypt these ciphers fast enough – it will take thousands of years.
STOP/Djvu Ransomware Distribution Methods
The unique part of this ransomware group makes it even stronger. Their affiliates master their tactics, and manage to find something new each month. Email spam, untrustworthy software, and hacked programs are not something new, but the way these crooks mask their stuff is amazing. They somehow manage to target their email spam attacks on the users who await the delivery messages. Knowing that there is a highly-demanded thing on torrents, they create a one-day site to spread the links to malicious torrent downloads. Such tactics allow them to catch each trend – and remain safe and sound!
Repacking for Stealthiness:
Anti-malware programs have a lot of ways of malware detection. Most widespread by underlying methods – database-backed detection – has a design flaw that allows the crooks to make their malware invisible for antivirus engines. It is a sort of obfuscation – but how graceful that is! Each new version of the Djvu ransomware has an entirely different code sequence. That makes the file hash, along with the file size and other attributes, completely different. They do such a trick using a unique repacking application that generates a completely new sample almost every minute. Meanwhile, the antivirus modules that detect an obfuscated code ignore that file – considering that there is no obfuscation in that file.
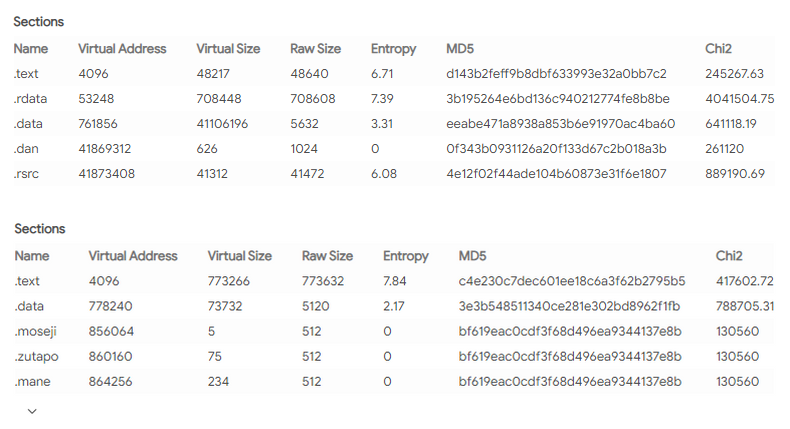
Even though analysts have successfully detected a regularity in the order of the changes implemented by that repacker, this ransomware is still uncatchable. They don’t leave literally a single clue to detect not only present versions but also further. Moreover, they sometimes change the repacking utility, leading to different file section sizes. The only hope for antivirus engineers to detect the STOP/Djvu ransomware is to use heuristic engines.
STOP/Djvu Ransomware Attack: Step-by-step
After the injection, this ransomware starts by … checking the location. First of all, this malware checks your region. If it is set for the following list of countries, it suspends itself from further execution:
- Russia
- Belarus
- Ukraine
- Azerbaijan
- Armenia
- Tajikistan
- Kazakhstan
- Uzbekistan
- Kyrgyzstan
Possibly, some of their distributors or developers are from these countries. That is a smart step to prevent any attention from local executive authorities. Russian hacker community even has a proverb “who attacks RU zone – gets a visit [of law enforcement] at the dawn”. Nonetheless, there are some cases when this check-up fails, and the user from one of these countries get his files ciphered. When the location check is passed, this virus connects to the command server and receives the decryption key and the victim’s ID. If the command server is inaccessible, ransomware uses the encryption key embedded in the exact ransomware file. That makes the file decryption possible – read the “Is it possible to decrypt…” paragraph.
Bring me action
After receiving the encryption key, the virus begins scanning your disk, searching for all files it can encrypt. Exactly, it manages to cipher all popular file formats – MS Office documents, Open Office ones, PDF, databases, Photoshop projects, videos, music, photos, archives, disk image files, etc. It does not encrypt all your files simultaneously. After detecting the folder filled with files, it stops the search and starts encryption. When the ciphering is over, it generates the ransom note in the folder, switches to the search mode, and repeats. It will attack both of your disks, including the files on your removable drives.
Finally, after ciphering all files it can find, it launches the delself.bat – the batch script file that creates a copy of the original ransomware files, adds them to the less suspicious directory (initial virus usually located in C:\Users\%username%\temp or C:\Users\%username%\Downloads) and removes the original ones. After that, a new .exe file is added to the Run registry hive, allowing the malware to run with each Windows start.
STOP/Djvu ransom note
ATTENTION! Don't worry, you can return all your files! All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key. The only method of recovering files is to purchase decrypt tool and unique key for you. This software will decrypt all your encrypted files. What guarantees you have? You can send one of your encrypted file from your PC and we decrypt it for free. But we can decrypt only 1 file for free. File must not contain valuable information. You can get and look video overview decrypt tool: https://we.tl/t-lj5qINGbTc Price of private key and decrypt software is $980. Discount 50% available if you contact us first 72 hours, that's price for you is $490. Please note that you'll never restore your data without payment. Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours. To get this software you need write on our e-mail: support@fishmail.top Reserve e-mail address to contact us: datarestorehelp@airmail.cc Your personal ID: ****************
What can I do to avoid being attacked by STOP/Djvu ransomware?
An obvious answer – use anti-malware software. Of course, a good one – that has a well-designed heuristic engine that can detect that sneaky ransomware. The tool with proactive protection is recommended. However, heuristics can be used in on-demand scans as well. One of the most demanded features is often database updates: this way, the program can detect even the newest STOP/Djvu ransomware variants.
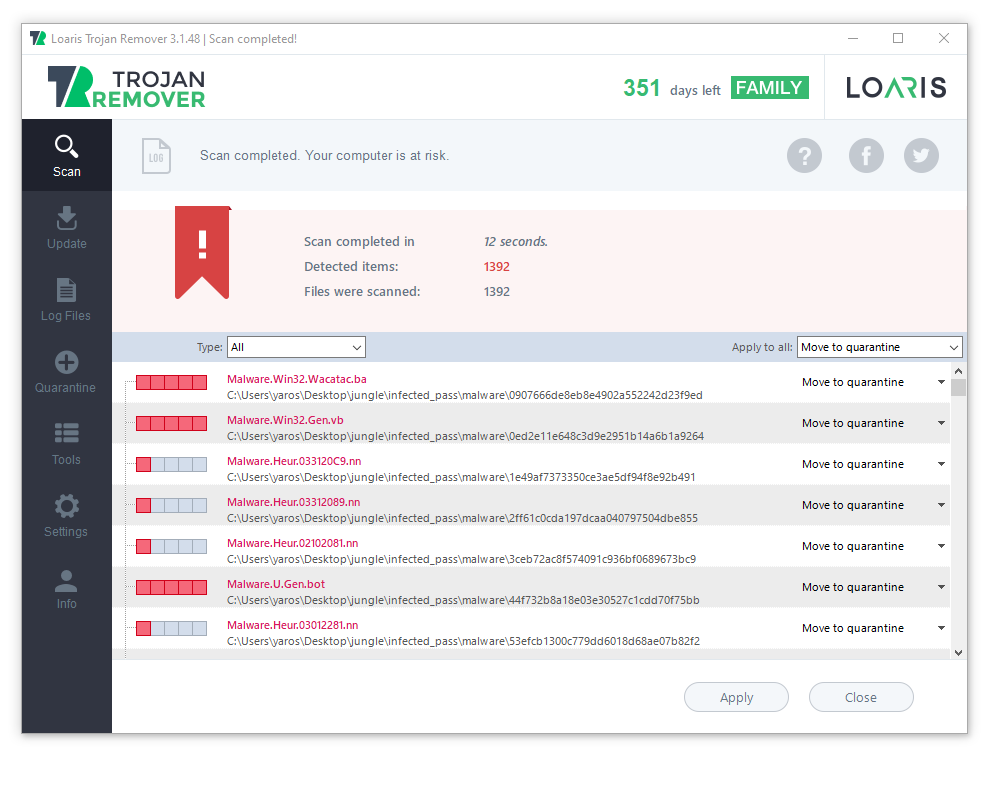
Nonetheless, even the most effective anti-malware tools will fail when you do everything to help the malware run successfully. Of course, you will do it unintentionally, thinking that you are just trying to launch the game or the program you have just downloaded from torrent-trackers. And it would be best if you kept an eye on what you are doing, remembering that no one will give you a paid program for free. Use programs with a good reputation when possible, do not use torrent trackers, and try to check the emails you receive twice before opening. That sounds hard and long, but each situation takes less than a minute . And this minute is always less than the time you will spend to get your files back.
 Is a real RED light for the different kinds of spyware
Is a real RED light for the different kinds of spyware
Is it possible to decrypt the files after the ransomware attack?
As I have already pointed out, it is impossible to decipher the files after the ransomware attack. The encryption algorithms it uses in the attack are extremely tough. The decryption with any “classic” methods, like brute force, for example, will take an extremely long time with any of the modern computers. However, the specific design feature of STOP/Djvu ransomware allows you to get some of the files back. The encryption module of that malware ciphers only the first 5MB of each file. It is enough for most of the files that this ransomware touches on your device to make them inaccessible. Nonetheless, high-quality music and video files are much bigger than 5MB. Yeah, the encrypted part is still unavailable – but there is much more information behind these megabytes. The only thing you need for that is proper software. In particular, WinAmp can launch such files. This very old piece of freeware is still demanded by many users – and, as you can see, it can be used for more.
Miracle decryption ability
Another way of getting access to your files requires a lot of luck. Sometimes, STOP/Djvu ransomware struggles to connect to its command server. This may happen because of your unstable Internet connection, as well as because of the troubles with the fraudsters’ servers. Thus, it uses a so-called offline key for file encryption. Since carrying all 2^256 keys is too much for tiny ransomware, the amount of offline keys is restricted, and a certain number of them is already known. Programs like Emsisoft Decryptor for STOP/Djvu can try to decrypt your files with these keys. Unfortunately, the chance that you will be able to get your files back this way is about 5%. In most cases,command servers work well, and neither does your ISP. Even setting up a network sniffer will not help you in any way. Besides the fact that it is not very ethical if someone else uses your computer, asymmetric encryption makes this sniffer useless.
File recovery tools – effective or not?
Another feature of the ransomware mechanism allows you to get your files back without decryption. STOP/Djvu ransomware creates a copy of each of your files, encrypts it, and then removes the original file, replacing it with the ciphered copy. And here comes the most interesting: just like with any other deleted file, you can perform a recovery operation with those affected by the ransomware.

How does that work?
Data storage technologies on both SSD and HDD disks suppose that the information will remain in the cells even after being deleted from the file system. Then, when you are writing something to your disk, these cells (or areas, if we mean HDD) will be re-used to erase the residue of removed files. Therefore, until these cells are reused and thus overwritten, you can try to get some information out of your disk.
Still, these tricks can be useless because of the technological features
Here, several things can make file recovery impossible. The first and most widespread issue is SSD usage. All modern OS versions have a TRIM command enabled for solid-state drives, which increases the disk’s lifespan. But this command cleans the cells where the deleted information was stored. Hence, there is nothing to recover. Another case that leads to an inability to get the files back with this method is when you use your PC after the encryption long enough to get the cells with the deleted files overwritten. That may happen even if your PC is idling. Windows has a lot of background processes that constantly write something to your disk and read the info from it. Hence, the less time you wait before the recovery – the more files you will be able to restore.
Shadow Copies. Another Way to Recover Your files
Volume Shadow Copies is a default Windows mechanism that allows the user always to have a backup copy of the system partition.2 That makes the system recovery possible in just several clicks since all important system files are backed up. And additionally, you can use this function to recover your files from this ersatz-backup. To reach it, you need to use specific software – such as Shadow Explorer, for example, .
The main problem of VSC usage is ransomware developers’ knowledge of this ability. Most of the STOP/Djvu variants you can find in the wild can disable and delete the shadow copies. Another thing that makes it a bit useless is that the copy is created daily by default. Hence, your backup copy may be overwritten by the ciphered files. And with each update of this backup, the previous copy is deleted.
- The report about ransomware-related losses in 2021.
- Official Microsoft guidance at Volume Shadow Copy service and its mechanism.