The majority of users are sure that the viruses are distributed separately. They believe you can’t download one trojan virus, which would contain 5-7 viruses of completely different types. Yes, such an opinion was actually in 2012…2014. However, it was completely wrong in 2023. Thanks to technological development, you can easily download a program declaring that it is capable of, for example, license key generation. Still, it will also deliver the stealer, miner, keylogger, spyware, and backdoor right in your system. It can differ from one case to another, but let’s have it all out first.
History of trojan virus: appearance
First mentions about the programs, who had the functionality that differs from the declared are dated in 19711. The first program had no malicious functionality a tall. Its name was “Trojan Horse” – after the famous horse dummy, which Greeks used to get into the city of Troy. Greek warriors were hiding under the guise of a wooden horse, left as a gift on the battlefield. Malware does the same -hides within the app which is legit at first sight.
Despite its early appearance, trojans’ development was not very fast. The main reason is that users had a superficial level of knowledge about so-called computer hygiene. They were downloading any files from the website they discovered yesterday. Typically they pay no attention to the file they download – even if it had an extension of .png.exe. It was straightforward to infect the needed amount of users without any tricks, so the trojan viruses were out of demand. However, several significant trojans were used for malware attacks in the 90s.
Time will melt it down
With the time flow malware injection came to be not so easy. Computer users became more experienced, antimalware software became widespread. Moreover, operating systems (generally Windows) became more protected against malware. So the malware distributors decided to use a known but low-used thing – trojan virus.
At the beginning of its way, one trojan was used to distribute the single type of malware. Such things as trojan-downloader (a type of trojan virus that acts as a downloader for other malware of any type) were not widespread. However, for adware/browser hijacker distribution, trojans were still out of demand: people clicked on colorful and blinking advertisements, initiating the downloading of so simple but annoying viruses; this scheme is even these days.
Actual types of trojan virus
Here is descriptions for all types of trojan viruses that were developed after the beginning of their active usage, and used even today:
- Trojan-stealer
- Trojan-spyware
- Trojan-encryptor a.k.a. ransom trojan
- Phishing trojan
- Trojan-backdoor
- Trojan-miner
- Trojan-stealer
Usually hides under the guise of “password keeper” or “system cleaner”, getting access to your passwords directly or through the cookies. Sometimes can be in its alternate form – keylogger, which steals not your passwords/logins, but all keystrokes.
Trojan-spyware virus
Tracks all your activities to sell it to someone else. Often used for personalized attacks, offered as a tracker for your children, spouse, or subordinates. It can offer such functions but does not decrease its malicious intent.
Trojan-encryptor a.k.a. ransom trojan virus
Contains a virus that encrypts your data and forces you to pay the ransom for files decryption. Because of the strong encryption algorithm, it is likely impossible to decrypt your files without specialized software.
Phishing trojan virus
Changes your hosts’ file and then shows you the fake variant of famous websites login pages, like Gmail, Facebook, Twitter, and so on, forcing you to input login/password. Malware creators will collect all information inputted on such websites.
Trojan-backdoor virus
Remote administration tool for your computer that is used to add your PC into the botnet or to inject you with more malware; creators of this malware usually pay a commission to the backdoor maintainers.
Trojan-miner virus
Uses your PC’s hardware capabilities to mine cryptocurrencies. A significant plummet may easily spot it in PC performance.
Facts and stats about trojans in 2023
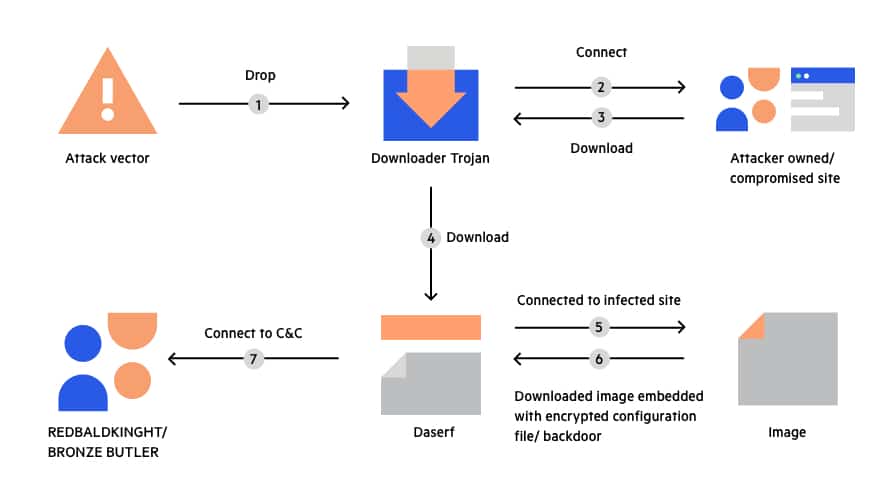
In the last three years, trojan viruses transformed significantly. Despite distributing every type of malware in a different trojan, trojan virus developers decided to pack several of mentioned types of malware inside the single trojan. The effect may be reached immediately after the trojan launch (if the malware files are right inside of the trojan program) or after some time (if malicious items are stored on the server). Last type of trojans is called “trojan-downloader”.
In combination with ransomware, trojan-downloader became an element of the cyber burglar chain. You get the downloader on your personal computer. Then your system becomes full of different malware. Downloader’s creators obtain the information they will sell and make your PC a part of the botnet, having their money from the botnet selling. When the majority of antimalware tools get the ability to detect and delete this downloader as well as all satellite malware, malware creators inject the ransomware, that is a perfect basis for the final payoff.
As you can see, trojan viruses are not so dangerous themselves, as dangerous the consequences which can be met after their activity.
How have I got the trojan virus?
The largest share of trojan viruses spreading is against programs with questionable and suspicious functionality (program crackers, Windows activators, et cetera). Programs of this type can have no declared functionality or have declared functions, but there is still a risk that there is a non-declared thing inside of this app. Such software is usually distributed on certain websites, full of applications with such properties, or through peer-to-peer networks – ThePirateBay, eMule, and so on. There is no chance to check if there are any malicious functions inside the program. The usage of described programs is done at one’s own risk.
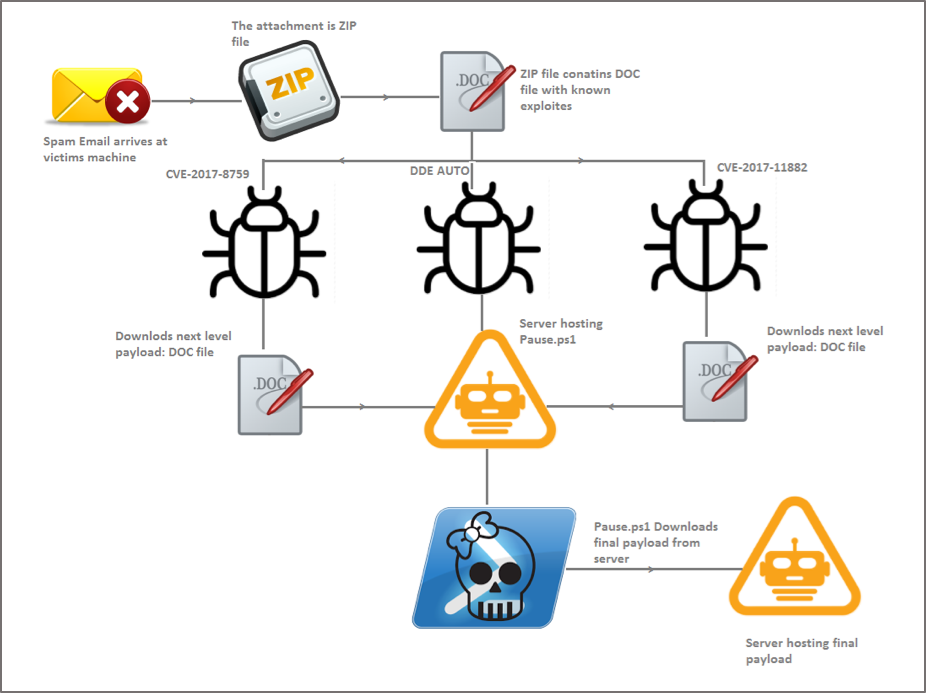
Another way of trojan spreading is archived Microsoft Office files and several other files which can contain different programs inside. These files can be found on different forums where you are looking for a solution for a problem on your PC, as well as ready materials on the theme you need to prepare for your university presentation.
How to defend yourself against trojans?
There are several quite effective methods which will help you to keep your PC safe. The majority of advice you can see below is a logical conclusion based on the text above.
Do not use cracked/unlicensed software. Their usage may lead not only to malware injection but also to numerous lawsuits. If you need to use such apps for some reason, test them on the virtual machine to ensure that they have the functions you need and are clean of viruses.
Have the antimalware program installed on your computer. Every computer with Windows onboard has an embedded solution – Microsoft Defender, but it is very vulnerable to malware like spyware or backdoors. These types of malware can disable the Defender by changing the Group Policies. So, it is recommended to use a separate antivirus, like Loaris Trojan Remover. It is named not just for a beautiful name: it has a serious database with about 97% of all existing trojan viruses, updating hourly. Be sure in your security while using Loaris.
 Is a real RED light for the different kinds of spyware
Is a real RED light for the different kinds of spyware
- Trojan viruses informationon Gridinsoft