The Domain Name System (DNS) is undoubtedly crucial to all companies that depend on the Internet. It is a critical element in the performance and legitimacy of an organization’s web applications and cloud services. Unfortunately, a loophole in your DNS can lead to hackers accessing user credentials and inaccessible content. That routinely leads to frustration and loss of users, to name a few. Such a hack has a common name of DNS Hijacking.
What is DNS Hijacking?
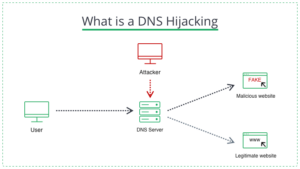
A DNS hijacking is a common type of domain server hack that targets a vulnerability in the stability of the domain’s server system on the network. This attack can either be on the DNS infrastructure, making it inaccessible or forcing website users to move to an alternate destination. In either case, these attacks use DNS as part of the attack strategy.
How Does DNS Hijacking Work?
A website’s domain name system is a unique, trusted protocol. However, many companies don’t take care to monitor their domains for malicious activity. Cybercriminals understand this and can initiate several attacks on an organization’s domain name system and get away with it. DNS converts human-friendly URLs into machine-friendly IP addresses. In this way, it allows users to match search queries to relevant websites. All devices connected to the Internet have an IP address consisting of numbers.
DNS fulfills the role of synchronizing domain names with the corresponding IP addresses, allowing Web site owners and users to choose easily remembered domain names and not to worry about machines being unable to communicate with those sites. For example, suppose you start a query by typing https://www.youtube.com/ into your search engine. In this case, the question will be sent from your computer to the appropriate DNS resolver, which is a computer that searches for the IP addresses related to your query. The DNS resolver communicates with high-level domain servers, looks for matches (for YouTube, this match is the 142.251.39.78 IP address), and sends them back to your device.
To execute the attack, attackers incorrectly resolve DNS to send your users to malicious websites. They accomplish this by hijacking routers, breaking the connection to the domain name server, or installing malware on users’ devices. When a company’s DNS is successfully compromised, the attacked users are redirected to a fake website. It means that the authorized IP address is translated into the illicit IP address of the malicious DNS hijacker.
Why Are DNSs Hijacked?
There are several reasons why the DNS can be hijacked. For example, a hijacker can use it for pharming, showing users ads to generate revenue, or phishing, directing users to a fake version of your website to steal data or registration information. Internet Service Providers (ISPs) have also been known to use domain redirection to manage user DNS queries to collect user data. Finally, some states and organizations use domain hijacking to censor or redirect users to alternative “allowed” websites.
Types of DNS Hijacking Attacks
There are several ways to conduct a DNS hijacking attack. Let’s take a look at the most common ones:
- DNS router hijacking: A DNS router is a hardware device that domain service providers use to map domain names to their corresponding IP addresses. Unfortunately, most routers come preloaded with default passwords that are usually not changed. Additionally, these devices can have a lot of firmware vulnerabilities. This can appear on hand for cybercriminals, and they can take advantage of weak passwords and vulnerabilities to take over the router and change the DNS settings. If the DNS router is successfully overwritten, it can quickly reroute traffic to another website and block your company website, making it inaccessible.
- “Man-in-the-middle” DNS hijacking: This is also called DNS spoofing. In this case, an attacker targets and intercepts the connection between a website’s traffic and DNS, changing the DNS settings and directing traffic to a malicious IP address.
- Local DNS hijacking: A local DNS attack installs malware on a client computer. Malware, usually Trojans disguised as legitimate software, gives cyber thieves access to users’ network configurations. This allows them to change DNS settings to direct users to malicious websites and steal data.
- Fraudulent DNS server: In this attack, the cybercriminal hijacks the DNS server and changes DNS settings to redirect traffic to fake websites.
How to Prevent DNS Hijacking
You can take many precautions to improve DNS security and prevent DNS hijacking. Let’s divide them into three main categories.
Prevent Name Server Hijacking
As previously mentioned, cyber thieves target DNS routers and reconfigure them to redirect traffic to malicious resources on the Internet. Therefore, the DNS server is a vital resource that must have robust security measures to prevent attackers from breaking in and launching attacks on website users. Here are some steps that the IT team can take to improve the security of your site’s name server.
- Install firewalls around your DNS resolver. Every DNS has resolvers, legitimate ones. However, attackers can install fake resolvers on DNS to compromise and hijack legitimate resolvers. It is recommended to place the original resolvers behind the firewall to prevent this and disable all unnecessary units. The less is the attack service – the less is the number of things to compromise.
- Increase restrictions on physical access to name servers. Unfortunately, even within your organization, there may be a traitor. Thus, the IT team should provide physical security, access with multi-factor authentication, and a robust firewall to limit access to the organization’s DNS.
- Prevent Cache Poisoning. General measures to prevent website cache poisoning include using upper and lower case in your organization’s domain name and randomizing server source ports, and randomizing the user ID.
- Fix known vulnerabilities immediately – Cybercriminals use obvious vulnerabilities to initiate DNS attacks. Therefore, your IT team is encouraged to periodically check DNS for vulnerabilities and patch them immediately to prevent attacks.
- Avoid zone transfers. DNS zone records are sensitive files containing data that attackers often aim for. As an example, hackers can impersonate subordinate name servers requesting a zone transfer, which involves copying the server’s zone records. To prevent this vulnerability, avoid zone transfers.
Mitigation for End Users
In addition to advertising hijacked traffic products, DNS hijackers also target user and credential theft. To keep yourself safe when web surfing, it’s a good idea to change your passwords regularly. In addition, keep your antivirus software up-to-date and use secure virtual private networks.
Mitigation for Website Owners
- Ensure secure access: Access to DNS should be restricted to only a few IT team members, who should have multi-factor authentication when accessing the domain name server registrar. This measure will significantly reduce the chances of DNS hacking. In addition, if it does not inconvenience the IT team, only a few Internet Protocol whitelisted addresses should have access to the domain name registrar.
- Client Blocking: To improve DNS security, some DNS registrars use client locks. Blocking disables the ability to modify DNS records unless the request is made from a specific IP address.
- Use a domain name service provider with DNSSEC: DNSSEC uses digital signatures and public keys to validate DNS queries. If your DNS registrar offers DNSSEC, turn it on to add a layer of protection that makes it difficult for attackers to intercept and redirect traffic from your site to a fake site.
Avoid Compromising Your DNS
DNS hijacking is a real threat that happens to vulnerable websites around the world. Despite significant efforts to prevent DNS spoofing and traffic redirection, attackers always find new, clever ways to access organizations’ networks and user devices, compromise data, and steal credentials. To avoid unpleasant consequences associated with DNS hijacking, your IT team must find and fix vulnerabilities before attackers. By performing a cybersecurity assessment and following the steps outlined in this article, you can detect malicious activity on your website and take appropriate steps to stop or prevent DNS hijacking.