Hardly anyone today can imagine life without the Internet. Unfortunately, as many more people use the Internet today than ever, Internet threats and vulnerabilities continue to grow along with this growing user base. That’s why it’s essential to know and take the necessary steps to protect your Internet traffic and data. In this article, we’ll look at DNS hijacking piece by piece: what DNS is and how to prevent and protect against DNS hijacking.
What is DNS?
The Domain Name System, or DNS, is a directory system that maps a website to its IP address. When you type a familiar website address into your browser (such as facebook.com), it sends that name – the Universal Resource Locator (URL) – to the DNS. This is known as a DNS query. In response to the query, your browser gets the IP address of the website – its exact numerical location on the Internet (for Facebook, it’s 157.240.22.35). Once your device receives the IP address, you can access and communicate with the site.
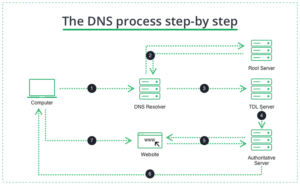
What Is a DNS Server? How Domain Name System Servers Work
What is DNS Hijacking?
DNS hijacking is the attack type where the hacker intercepts DNS requests and redirects users to malicious sites. Cybercriminals are not the only ones who use DNS. Some Internet Service Providers (ISPs) also hijack your DNS to redirect traffic to suit their purposes. Not so long ago, DNS hijacking was considered a relic of the past. However, many companies and organizations have been targeted by DNS hijacking, including Gmail, Netflix, and PayPal. Even though all DNS hijacking activities bear upon the same basic principle, there are slight differences in how crooks carry these attacks out. We’ll look at them next. The site’s full name we enter into a browser is the Fully Qualified Domain Name (FQDN). It consists of several parts: a top-level domain (TLD) (e.g., .com .net .gov), a subdomain (.facebook), and a host (www). Each has a corresponding DNS server involved in the DNS query process.
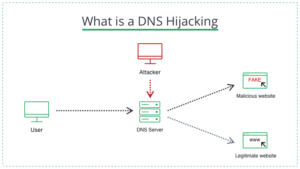
What is a DNS Hijacking
First, your browser queries the DNS resolver – the first server – for the location of the domain. The resolver then passes this request to the TLD DNS server, which then queries the DNS server that belongs to the website. Thus, hijacking can happen anywhere in this “chain”. Today, you will likely use the DNS configurations set by your provider. ISP theoretically can use the settings to collect data and redirect you to sites and content that benefit them. More nasty forms of DNS hijacking include compromising DNS servers and adding fake IP addresses to redirect users to the wrong locations. Because DNS queries are often overlooked, such attacks can be challenging to counteract. Moreover, because DNS queries work, where each participating server requests help from one “further down the chain” to find an address, complete DNS hijacking can spread quickly, affecting many users and servers.
Types of DNS Hijacking Attacks
In general, there are five types of DNS hijacking attacks:
1. Man-in-the-middle Attack
This is a classic attack, synonymous with DNS hijacking. The attacker intercepts the user’s DNS request and redirects it to his DNS server. This server then uses the Trojan to return the wrong IP address, sending you to a “fake” website. “Fake” websites are designed to be very similar to the target website to fool the victim. Hackers will steal any information the victim enters on these sites. This subsequent exploit is known as “phishing” and can be done after any DNS hijacking.
There is also another type of attack known as “pharming.” It can be launched using a man-in-the-middle attack or any other capture method described below. This attack aims to display unwanted ads and pop-ups. This is done to redirect the victim to generate ad revenue. This structure of the DNS query process provides several potential entry points for cybercriminals looking to perform a man-in-the-middle attack. Unfortunately, by default, when the response reaches your device, there is no way to check if the DNS query has been changed.
2. Malware Attack
Perhaps the most common type of attack today. An attacker infects the victim’s device (phone, tablet, computer, or router) with trojan viruses. These change the DNS settings of the infected machine and redirect the victim to a malicious DNS server. This attack is considered a local attack because it is initiated directly on the victim’s device. On the other hand, the man-in-the-middle attack, which compromises the request on that part of the process, takes place outside the local network (LAN).
3. Cache Poisoning
This is another way for the attacker to redirect the victim to a “fake” site without directly intercepting DNS requests. Fake DNS entries are stored in the cache (memory) of the victim’s local DNS resolver, redirecting her to dangerous fake sites instead of the real sites requested. Because the DNS resolver handles queries from all devices on the LAN, a well-planned cache poisoning attack can compromise the entire LAN and those who use it. One user clicking on a malicious link in an email or pop-up window can lead to many problems.
4. Fraudulent DNS Server
A type of attack where a DNS server is attacked and hacked, and its records are changed to redirect incoming requests to fake sites.
5. DNS Hijacking Using Router Vulnerabilities
This attack involves someone gaining direct access to the victim’s router and then modifying its DNS settings, redirecting traffic to compromised DNS servers. These servers can turn traffic on the local network into dangerous phishing sites. Although this attack may seem similar to malware attacks that infect a router, these attacks are initiated directly at the router. Malware attacks tend to indirectly compromise a victim’s router by first infecting their device.
How to Stop DNS Hijacking?
Fortunately, it’s pretty easy to do, and tools and techniques are available to protect yourself against DNS hijacking. They are similar to those used to protect against other common vulnerabilities. As a primary defense against DNS hijacking, it is recommended that you do the following:
- Use reliable security software. Also, constantly update your system, software, and anti-virus software. Do not click on dubious links in emails or on social networks.
- Change your router’s default administrator login and password. These credentials should not be the default ones. Also, the login window is better to move from the default 192.168.0.1 or 192.168.1.1.
- Don’t use public Wi-Fi networks to send or receive personal information or to log in to sites that require credentials. Such networks are ideal for MITM attacks. Using a network that has no security settings exposes your privacy.
- Always check the URL of a site to make sure that it is the site you intended to visit. If any part of the address looks suspicious or unfamiliar, close your browser and check your DNS settings. Fake sites do not have a valid SSL certificate. Ensure the site you use has an SSL certificate, indicated by the padlock icon in your browser address bar. If the website does not have a valid SSL certificate, never enter personal information (e.g., credit card details, personal information) into a web form on such a site.
Although the above steps will help protect you from DNS hijacking, these attacks are varied, and new vulnerabilities continue to be exploited. You use them frequently if you can remain vigilant for unusual pop-ups and messages on pages. Unfortunately, you have no way to prevent DNS server compromise.
How to Protect Yourself from DNS Hijacking
For these reasons, the safest and easiest way to protect yourself from DNS hijacking is to use a VPN from a premium provider. Virtual private networks were conceived to gain secure remote access to local networks. Today, however, their use and benefits go far beyond that. A VPN creates a tunnel and encrypts all of your traffic that passes through it. It also bypasses your router settings and performs DNS queries using VPN DNS converters. In addition, the best VPNs offer advanced DNS protection to ensure that all your DNS requests are routed through their DNS servers. These virtual private networks also block traffic to DNS servers provided by your ISP, government surveillance agencies, or cybercriminals.
 Is a real RED light for the different kinds of spyware
Is a real RED light for the different kinds of spyware
For example, some virtual private networks offer browser extensions. In contrast, others provide more secure “tunneling” protocols, such as IPsec, to ensure that no DNS requests are intercepted and that all your traffic is sent through a secure tunnel. Be careful when using free VPNs, as many can log your activities, track your online activity, and flood you with ads.
The problem of DNS hijacking is often overlooked. Therefore cybercriminals use it to redirect you to dangerous “fake” sites. As a result, DNS queries are largely ignored, as well as the potential harm that can be done if they are compromised. But DNS hijacking is not limited to criminals. ISPs also use modified DNS servers to redirect your traffic in their favor. They often do this to gather statistics or may send you ads when you access unknown domains.