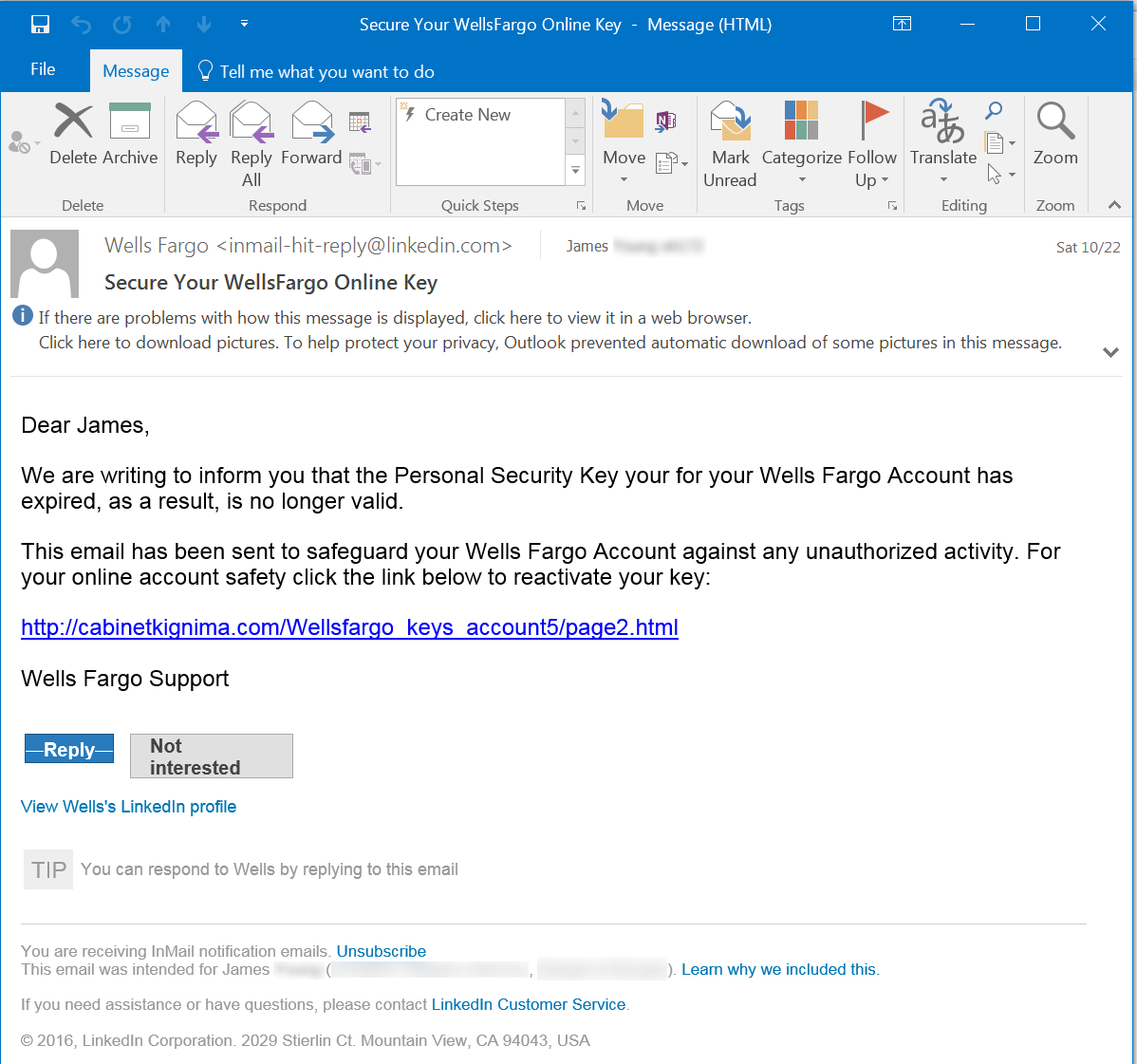
Whaling is a particular type of phishing that is specifically directed towards different companies’ and organizations’ executives. Threat actors may pretend to be an executive of some companies and so target other employees of that company or they will try to target an executive director. In this type of phishing attack, threat actors rely on complex social engineering attacks to get to their goals. They know that these days most executives apply various phishing mitigation strategies and tools so they need to be extra stealthy in their approaches.
Unfortunately for companies and organizations around the world it can be difficult to trace the attackers as they often disguise their physical location and sweep their digital footprint.
What Is The Difference Between Phishing And Whaling
We said that whaling is a specific kind of phishing that targets high-profile people in different companies and organizations. In whaling, threat actors use various mediums to lure victims into their scheme like voice calls, text messages, emails, etc. The same goes for other subcategories of phishing where this or that medium will be prevailing.
Generally speaking, phishing includes many subcategories including angler phishing, smishing, vishing, spear phishing, email phishing and of course whaling.
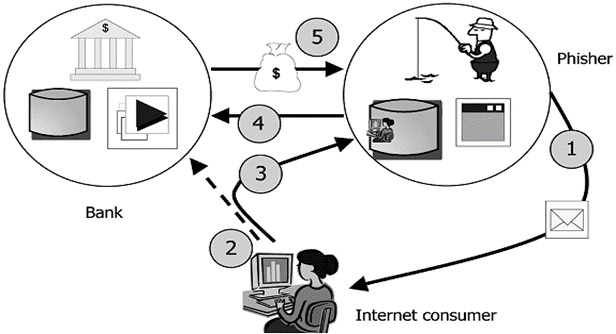
Visualization On How Whaling Works
Phishing has become one of the biggest threats that not only modern companies and organizations face but also ordinary users suffer no less. Many know or at least have an Idea of what phishing and we also here talking about whaling is either to steal some sensitive and valuable information or infect targeted devices with malware.
Or the aim of a phishing attack can be both. Not only do common scammers take advantage of phishing but also APT actors widely deploy this kind of attack in their more sophisticated maneuvers. And one moment to mention: people also often get confused by the term ‘Spear Phishing‘ which it seems means the same as whaling but in reality there’s a slight difference between the two of them.
What Is The Difference Between Wailing And Spear Phishing
There’s no such a big difference in reality between the two terms. Both of them are phishing species and both aim to steal valuable information or install malware. However, whaling threat actors target only high-profile individuals. In spear phishing, it can be various people, depending on the information hackers have. Within the latter, threat actors “tailor” their emails, voice calls, and messages to the victim’s personal profile. They specifically adjust the attack using publicly available information, in order to make it look trustworthy. Whaling threat actors make their targets only high management personnel but also make thorough research on such individuals.
How Does Whaling Work
First goes the intelligence gathering phase where threat actors will do research on their future victims. For example, they will closely inspect some CEOs’ LinkedIn profiles and take from it some info to appear more personal to their target.
Apart from this threat actors may also do a research into the sphere of professional jargon. That helps to appeal to the victim’s perception and disguise phishing email as a professional one. That is what about the first step of whaling then comes the next one when threat actors conduct the actual phase of an attack.
Usually they will do it in one of the following attack vectors:
- Baiting. Almost a trick from some movie but such instances really are. Threat actors will leave an authentic-looking USB drive in a gym, at the workplace, or mail it to the victim; all to make them insert the thing into their computer;
- Pretexting. Threat actors sometimes go into full acting school to get to their aim. They befriend their future target on some social media pretending to be an industry peer, love interest, business partner, or some authority figure;
- Phone calls. Simple phishing trick when threat actors call their victims to reinforce the previously sent email;
- Email messages. The main medium for phishing attacks among threat actors. They use malicious attachments, websites and links.
What Is The Purpose of Such an Impersonation?
No wonder that with such high-profile targets in mind, threat actors can expect to accomplish various tasks and have much more broad possibilities out of the attack. In targeting CEOs or pretending to be one and targeting their employees on behalf of faked CEO correspondence threat actors can have the next goals accomplished:
- Personal vendetta. Although this might be a rare goal, it happens. Someone can have the simple desire to put in dirt other person’s reputation;
- Malware. Whaling can be done with the goal to make victims install a different kind of malware like keyloggers, rootkits or ransomware;
- Corporate espionage. With successfully accomplished whaling attack threat actors can gain an access to trade secrets, steal some intellectual property; all to help business competitors that can even reside in another country;
- Supply chain attack. This attack occurs when threat actors find a vulnerable element in some businesses or organization’s supply chain and hit it to bring damage to the whole structure. Such attacks via whaling is also done against governments when threat actors can theoretically target its vendors;
- Control. One of the main tasks in whaling is to get valuable credentials that later can use for installing a backdoor into a network or for lateral movement across the compromised network in a ransomware attack, for example;
- Money. In a successfully done whaling threat actors can trick victims into paying money via a wire transfer or force an organization or business to extortion after previously conducted data exfiltration.
What Are The Most Known Examples Of Whaling
Here are some of the most famous examples of ‘successful’ whaling attacks:
- Threat actors attacked the Australian co-founder of a hedge fund with fraud. As a result, the company was forced to close;
- In an attack on one small business owner threat actors managed to steal a sum of $50,000 out of the business;
- A CEO from Australian aerospace manufacturer FACC lost $58 million after getting a victim of a whaling scam;
- The famous giant toy manufacturer Mattel wired $3 million to threat actors after one of its finance executives received a fraudulent request from a seemingly newly appointed CEO;
- Hong Kong-based company of wireless devices Ubiquiti Networks Inc. got scammed for $46.7 million after one of its employees received a fake email.
How To Prevent Whaling
To effectively defend yourself against whaling attacks and don’t risk the cybersecurity of businesses and organizations CEOs and employees as well should consider the next generally accepted rules on how to avoid whaling:
- Download and install anti-phishing software. Although social engineering tactics including whaling heavily rely on human error but for companies and organizations to have some anti-phishing software in place will be a useful consideration;
 Is a real RED light for the different kinds of spyware
Is a real RED light for the different kinds of spyware
- Have social media education sessions. The rule is simple and generally doesn’t concern only high management personnel but all users on social media. On some people’s social media accounts, threat actors can even without breaking into their devices gain a lot of valuable information. That’s why everyone on social media should limit what personal information they share and can actually view it;
- Set data protection policies. Have set monitoring of all income emails for signs of potential maliciousness. All those that don’t look safe shouldn’t be allowed into the income box, but instead redirected to spam email one.
Also teach your employees and yourself about how you can in general discern if any email sent is malicious or not; - Multi Step verification. All requests for access to confidential information or permission for wire transfers should be filtered through multiple layers of verification before receiving consent. Check all emails and attachments for maliciousness and possibly other issues outside organization/ business;
- Raise employee awareness. It should also be in company’s employees responsibility to protect its assets from cyber security attacks. Teach them on how to discern not only whaling attacks but also other kinds of cyber threats.
Employees should know what social engineering attacks are and what tactics cyber actors use to conduct them successfully.
Don’t also forget about any requests for money transfers being asked from suspicious emails.