Social engineering is a type of cyberattack that instead of software vulnerabilities aims for vulnerabilities in human psychology. It implies various psychological tricks to lure victims into making security mistakes like giving away some sensitive information. And that is what makes social engineering attacks especially dangerous. The mistakes humans make after the psychological pressing are harder to predict or prevent than some cyberattacks.
Threat actors perform social engineering in multiple steps. Initially, they try to find any possible entry points or weak security protocols in order to begin an attack. After completing the first step, threat actors will proceed with things like gaining the trust of a victim. Then, crooks will use the information they lured out to get into the victim’s accounts.
What Kinds Of Social Engineering Attacks Are
Social engineering attacks can be of various kinds and threat actors can use them anywhere where interaction with humans is involved. Below are the most common social engineering attacks you should be aware of in order not to get caught by them easily:
Spear phishing
One of the most common kinds of phishing attacks where threat actors specifically chose their future victim. They do thorough research on their target like job position, characteristics, social media, friends list, etc. They perform all these steps in order to create a highly-convincing malicious email, that will look legit to a specific person. Spear phishing attacks might take months of preparations before launching an actual attack. But they are harder to detect and have much better chances for success if threat actors are skilled enough.
After having done their research, threat actors will tailor authentically looking emails or messages in social networks. It should look like something it’s waiting for. Classic examples are delivery notifications or updates regarding the documents issued. Crooks add a malicious attachment or link to infect the victim’s device with malware or lure out credentials or login information.
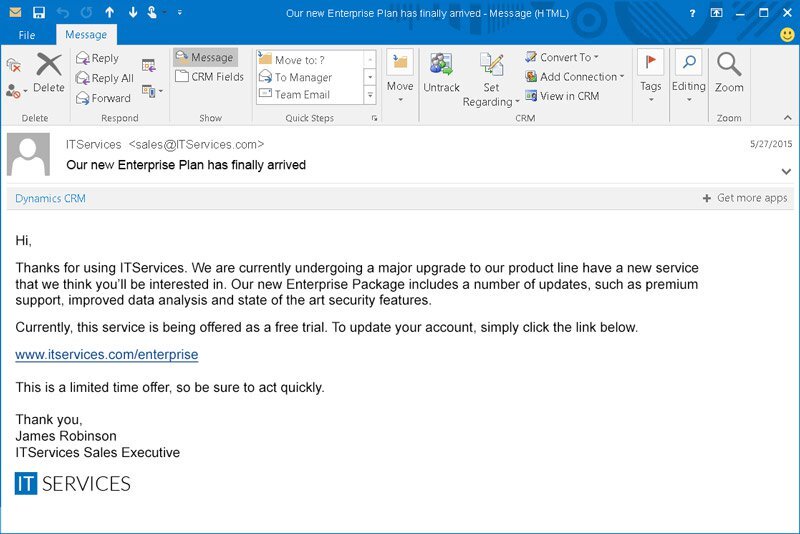
Classic phishing
A similar method of getting confidential information through malicious email messages. Here the same threat actors create an email that causes a sense of urgency, fear, or curiosity in victims. The malicious email will ask its recipient to click a link or open an email attachment. Both of them contain either malware or malicious website, which does not carry any good to the user. In some cases, crooks bait the victim to start mailing, luring out all sensitive info in a direct way.
Pretexting
This trick supposes SMS or phone calls as the main application way. Crooks are trying to get the information from you pretending to be the official of some sort. It may be a phone call, where someone tries to mimic the bank and ask for your personal details. At the end of such a call crook will “suddenly” understand that it got a wrong number. Nonetheless, it already holds all the information.
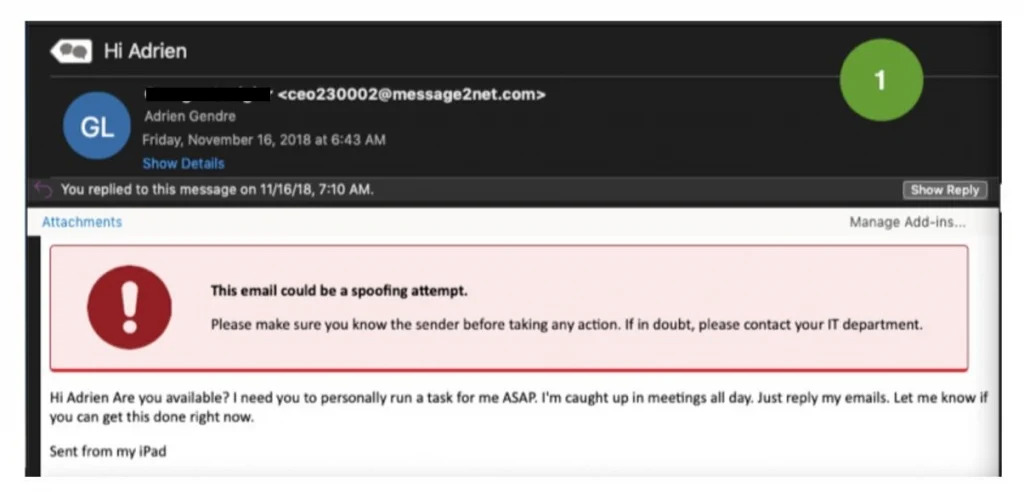
Typical example of a pretexting message
Similar story is about SMS or messages in social networks. Crooks pretend to be representatives of online shops and wish to clear out your order. Some sophisticated cases can have a disguise of your landlord. They can also pretend to be your co-workers, police, or tax officials. With this trick threat, actors can get to know social security numbers, bank records, phone records, personal addresses, staff vacation dates, etc.
Scareware
This kind of malicious software is also referred to as fraudware, rogue scanner software and deception software. If you’re infected with this social engineering malware you will experience frequent alarms or notifications that your system is infected and you need as fast as possible remove the threat.
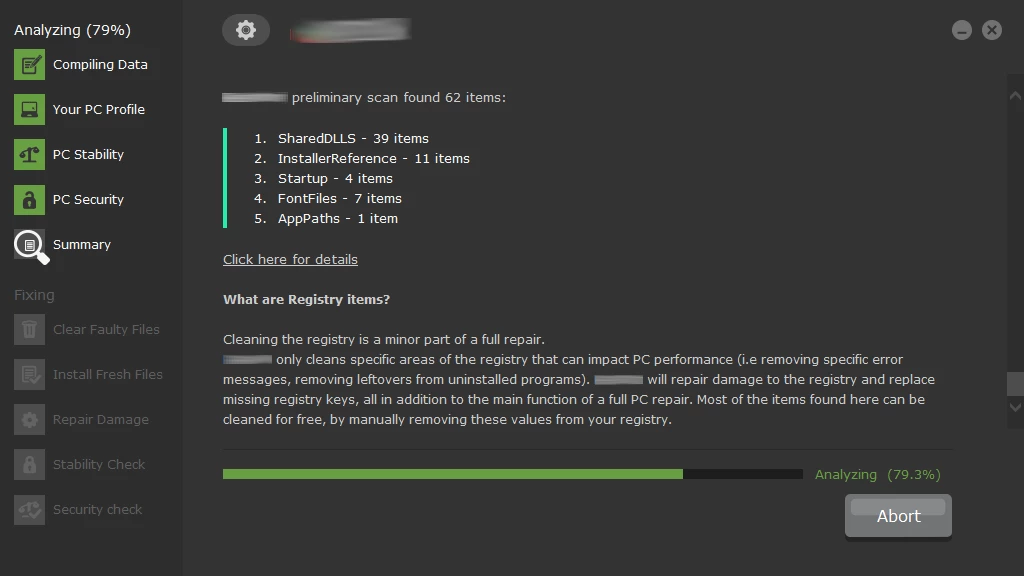
Scareware detections example. It will find problems even in a fresh Windows installation
To get rid of the problem scareware will instantly offer you a solution — some software that most likely is malware itself or really doesn’t do anything related to antimalware software because it is simply useless. With scareware, you either will lose your money or get infected with another malware. Scareware gets often distributed via spam emails offering victims to buy useless/ harmful software or displaying constant warnings that something is wrong with the system.
Baiting
Usually comes in a form of enticing ad that tries to lure potential victims into installing some malware infected application or will redirect to a malicious website. This social engineering attack exploits human feelings of curiosity or greed and thus luring victims in a trap and stealing their personal information or infecting them with malware.
How To Prevent Social Engineering Attacks
Keeping up to some cyber security rules should help you to avoid being the victim of social engineering:
- Regularly update your antivirus/antimalware software. Make it a habit to regularly check for your antivirus/antimalware updates or set an automatic update if this option is possible. See if the updates have been applied and also run regular scans for possible infections;
- Be cautious around various offers. If anyone approaches you either via social media or messengers be attentive to what this person offers and who this person might actually be.
Google the topic of your conversation and the results should give you a hint as to what actually you are dealing with; - Enable multi-factor authentication. One of the most valuable things threat actors are going for is your credentials. So it will be only wise to enable for your most important accounts the mechanism of multifactor authentication in case your credentials get stolen or leaked;
- Make it a habit not to open emails or attachments from suspicious sources. Even if you received an email from someone you know, it’s better to cross-check and directly ask the person who sent you this email.
In case you received an email from your service provider check the info on their official website or call the support line.
Emails are one of the most popular mediums for social engineering attacks and this kind of correspondence gets faked the most so be extra cautious won’t be too much.