Every email user knows what a phishing message is. Such an email usually contains a request to perform an action and to do so immediately. The main attributes of phishing emails are urgency, the presence of a link that the user is asked to click, or an attachment that the email’s author is requested to open. A business email compromise is almost the same, only at the enterprise level.
What Is a BEC?
A business email compromise is a type of cyberattack where attackers pretend to be a trusted person to deceive employees or customers into doing something they want. This could be paying, sharing data, or giving away sensitive information. The FBI’s 2022 Report says BEC is one of the fastest-growing and most financially damaging cybercrimes. For example, in 2021, losses from BEC attacks exceeded $2.4 billion, a 566% increase since 2016, according to the Internet Crime Complaint Center (IC3). As more people work remotely and communicate digitally through channels like email, experts predict that BEC attacks will continue to increase.
Most Popular Types
According to the FBI, here are some common types of attacks that cybercriminals use to steal information or money from companies:
- Account Compromise. In this case, an employee’s email account is hacked and used by the attacker to request payments on behalf of vendors. The funds are then transferred to accounts owned by the attackers.
- Attorney Impersonation. Cybercriminals may pose as lawyers or legal team members to manipulate new or junior employees into taking action. For example, it can be sending data or requesting a wire transfer. They typically frame the request as urgent or confidential, making it difficult for inexperienced employees to validate it.
- CEO Fraud. Similar to attorney impersonation, the attacker poses as the CEO. They target finance team members and claim urgent support on a time-sensitive or confidential matter. The employee is then tricked into transferring money into an account controlled by the attacker.
- Data Theft. In this case, attackers target a company for data. The attacker most commonly zeroed in on HR or finance team members. Thus he attempts to steal personal information about the company’s employees or customers. As a result, this information can be sold on the Darknet or used to inform and advance future attacks.
- Fake Invoice Scams. Cybercriminals pose as vendors and request payment from employees for service. They may edit an official vendor invoice template and alter the account details so that funds are transferred into an account owned by the hacker.
Common BEC Techniques
Attackers who engage in business email compromise use several tactics to carry out their attacks. The three most common methods are:
- Domain Spoofing. This type of phishing involves an attacker impersonating a known business or person using a fake website or email domain. The goal is to trick people into trusting the attacker. The domain may appear legitimate, but upon closer inspection, it may have subtle differences that reveal its fraudulent nature (for example, roly.kelly@domain.com and roly.kelley@domain.com). As a result, users who interact with the site or message may unwittingly disclose sensitive information, send money, or click on malicious links.
- Social Engineering. This tactic involves manipulating people to take a desired action, such as sharing confidential information. Attackers use powerful motivators like money, love, and fear to convince people to comply with their requests. In addition, they may offer false opportunities to fulfill these desires.
- Compromised Accounts. This method involves an attacker breaching an email or system account using social engineering, malware, or password-cracking tools. Once they have control, they can carry out any activity on behalf of the owner.
BEC attacks can target any company, especially those with inefficient processes or short approval chains. Individuals like C-Suite executives, finance team members, HR leaders, and new employees are often targeted. These employees hold valuable information and are more susceptible to manipulation or unfamiliar with internal processes.
BEC detection issues
Unfortunately, some BEC attacks are challenging to detect for several reasons:
- They are low-volume, often consisting of only one or two emails, which can be carried out without generating an unusual spike in email traffic. This low volume also enables the attackers to regularly change their source IP address, making it harder to block the campaign.
- BEC attacks use a legitimate source or domain, which allows them to bypass IP address blocklisting. They also employ domain spoofing to make it appear that the emails originate from a natural person.
- These attacks may come from a legitimate email account, which requires significant effort on the attacker’s part.
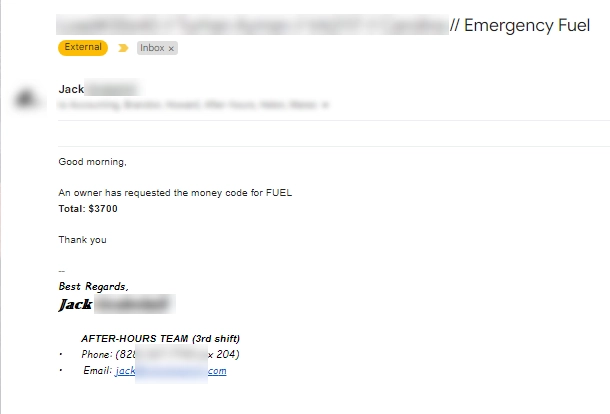
This email is an Illustration and not a screenshot of real BEC spam. But usually, emails that are sent after a compromise are no different from the real one
Thus, BEC campaigns can pass DMARC checks as organizations may not have configured DMARC to strictly block emails, or attackers may send emails from a legitimate source.
Signs of Business Email Compromise
BEC emails are usually short, without links, attachments, or images, and aim to trick the recipient into taking a specific action, such as transferring money or giving unauthorized access to sensitive data or systems. Standard features of these emails include:
- Urgent language.
- Impersonation of important figures within the organization.
- Providing a reason for the necessary request.
Attackers also give specific instructions on where to send the money and how much to send. They may also instruct the victim not to contact the sender or confirm the request with anyone else to avoid getting caught.
Protect Your Company Against BEC Scams
Because BEC attacks don’t use digital tools like malware or viruses, they rely on a human-to-human connection. This makes them tricky to identify and challenging to prevent with traditional security tools like antivirus solutions or endpoint detection and response. Since BEC attacks are centered around people, it’s essential to use protection and prevention methods focused on humans. Here are some tips that help to guard against these attacks:
Employees training
Organizations must train their employees in robust cybersecurity measures to protect against BEC attacks. This training should include modules on social engineering techniques, and the organization may also want to test the effectiveness of the course through simulations or drills. In addition, the training should cover essential points such as recognizing unusual or inappropriate executive requests, proper procedures for financial transactions and vendor invoices, and identifying spoofed email addresses or domains. Employees should also learn to identify tactics attackers use, such as fear, intimidation, confidentiality, and urgency to manipulate them.
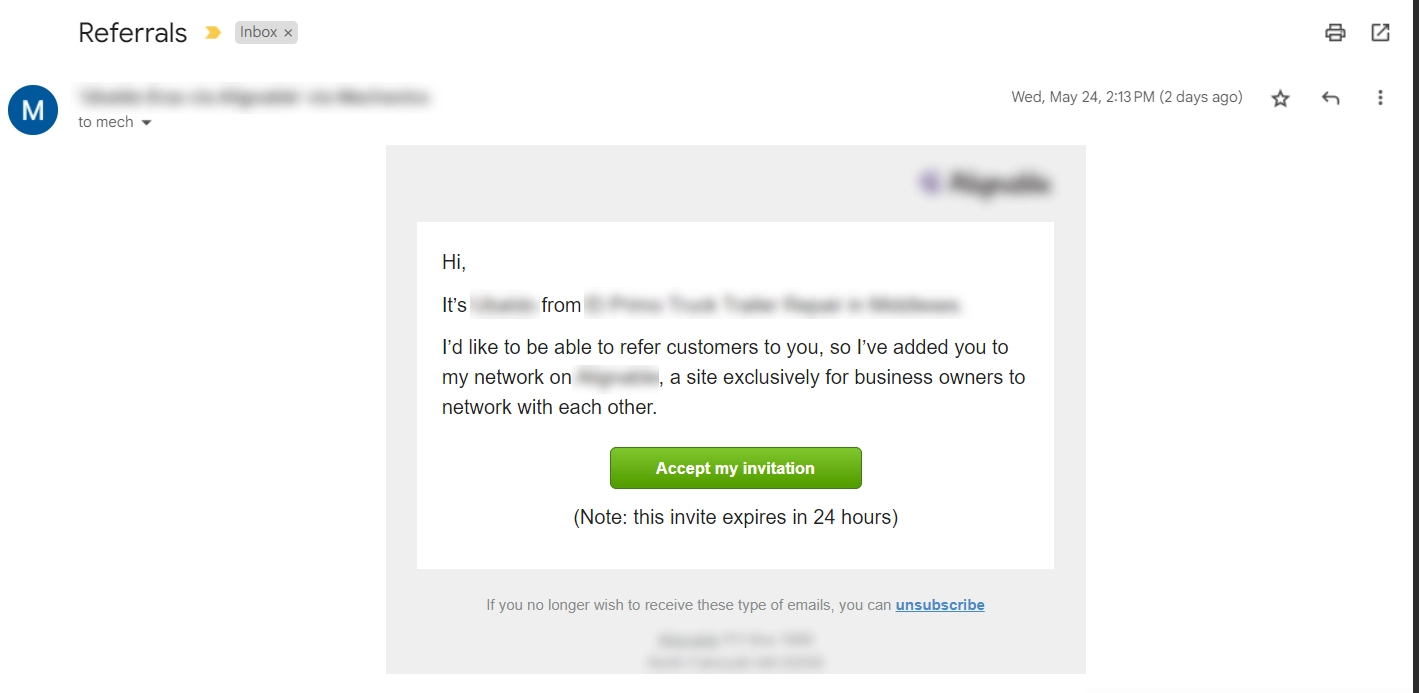
This email is also an illustration of a phishing link email. When you receive such emails, looking carefully at all the details is essential.
Apply using 2FA on all business accounts
Two-factor authentication is probably a highly secure method that uses two layers to verify a user’s identity. Instead of relying solely on a password, 2FA requires a code to be sent via text message or generated through an app. This additional step ensures that only authorized users can access their accounts. Multi-factor authentication (MFA) takes this effort further by requiring two or more authentication layers to grant access to an account. In addition, when logging in, the system will give an approximate location device from which the login was made.
Change passwords regularly
No one likes to work with passwords, but they are necessary to keep your accounts secure until something better comes along. Common sense says you should always use a different password for multiple accounts at a time. In addition, you should change your passwords periodically for maximum security. How often you should change your passwords depends on their complexity. For example, if you use a strong password that is difficult to brute-force guess, you do not need to change it too often. However, there are cases when a password needs to be changed asap. This is usually the result of leaked passwords.
Use Zero Trust
Zero Trust is a security concept ensuring all users are verified and authorized before accessing applications and data. This involves using advanced technologies such as multi-factor authentication, identity protection, endpoint security, and cloud workload technology to verify a user or system’s identity, check their access credentials, and maintain system security. This approach is crucial in preventing Email Account Compromise (EAC), where malicious actors impersonate legitimate users to gain unauthorized access.
Monitor actors who leverage BEC as an attack
It can benefit big companies with many potential risks to monitor the hackers and cybercrime groups who use BEC. However, this usually requires working with a reliable cybersecurity provider to help the company pinpoint the culprits and methods that pose the biggest threat. For example, suppose an accountant receives an email supposedly from the CFO. In the email, the CFO asks the accountant to buy some gift cards and send them to the email address of a prospective client. In addition, the CFO asks to do this asap, specifying that he is getting on a plane and will not be available for the next few hours. However, given the atypical nature of the request, the accountant decides to call back and clarify. As a result, the CFO has no idea what kind of request he is talking about. Thus, the BEC attacks attempt is a complete failure.
Protect Yourself Against BEC Scams
To avoid business email compromise, you must be cautious about the information you share online or on social media. Scammers can use details like your pet’s name, the schools you attended, your birthday, or links to family members to guess your password or answer your security questions. If you receive an unwanted email or text message asking you to update or verify your account information, don’t click on any links. Instead, look up the company’s phone number and call them to check if the request is legitimate. Before responding to any correspondence, double-check the email address, URL, and spelling for any discrepancies scammers might use to gain your trust. Be careful about downloading any attachments, especially from unknown sources. Whenever possible, enable two-factor or multi-factor authentication on your accounts and never disable it. If you receive a payment or purchase request, verify it in person or by calling the person to make sure it’s real. And be extra cautious if you’re being pressured to act quickly.